Cloud migration security refers to the measures taken to ensure the security and protection of data and applications during the process of moving from on-premises infrastructure to a cloud-based environment. As organizations increasingly adopt cloud computing, the need for a robust security strategy during the migration process becomes crucial.
Moving to the cloud offers numerous benefits, including scalability, flexibility, cost savings, and improved efficiency. However, organizations must carefully plan and implement security measures to mitigate potential risks and ensure that sensitive data remains protected throughout the migration.
One of the primary concerns during cloud migration is data security. Data stored in the cloud is subject to various threats, such as unauthorized access, data breaches, and data loss. To address these risks, organizations need to implement comprehensive security measures, including encryption, access controls, and data backup and recovery mechanisms.
Encryption is a critical component of cloud migration security. It involves converting data into a form that is unreadable without the use of a decryption key. By encrypting data before it is transferred to the cloud and ensuring that it remains encrypted while at rest and in transit, organizations can prevent unauthorized access and maintain the confidentiality of their data.
Access controls play a vital role in cloud migration security by ensuring that only authorized individuals can access and interact with the migrated applications and data. Organizations can implement measures such as strong authentication, role-based access controls (RBAC), and multi-factor authentication (MFA) to authenticate users and restrict access based on user roles and responsibilities.
Another aspect of cloud migration security is data backup and recovery. Organizations must have a robust backup strategy in place to ensure that data can be restored in case of a data loss event or system failure. Backups should be stored securely, preferably in a separate geographic location or cloud region, to protect against data loss due to natural disasters or other catastrophic events.
In addition to these technical security measures, organizations should also consider compliance and regulatory requirements during cloud migration. Depending on the industry and location, organizations may be subject to various data protection laws and regulations, such as the General Data Protection Regulation (GDPR) in the European Union. It is crucial to ensure that all necessary security controls and data protection measures are in place to comply with these requirements.
Cloud migration security also involves assessing the security posture of the cloud service provider (CSP). Organizations should evaluate the CSP’s security practices, certifications, and compliance with industry standards before selecting a provider. It is important to understand the shared responsibility model, which outlines the division of security responsibilities between the organization and the CSP. This understanding will help organizations determine the security controls and measures they need to implement on their end.
Cloud migration security is essential to ensure the confidentiality, integrity, and availability of data and applications during the migration process. Organizations must implement a comprehensive security strategy that includes encryption, access controls, data backup and recovery, and compliance with regulatory requirements. By considering these security measures and partnering with a trusted CSP, organizations can achieve a secure and successful cloud migration.
CHECKPOINT
Check Point Infinity architecture delivers consolidated Gen V cyber security across networks, cloud, and mobile environments.
- Architect for Cloud Security
- Leverage Native Cloud Solutions
- Monitor and Automate from the Start
- Implement Continuous Compliance
- Minimize Your Security Solution Footprint
FORTINET
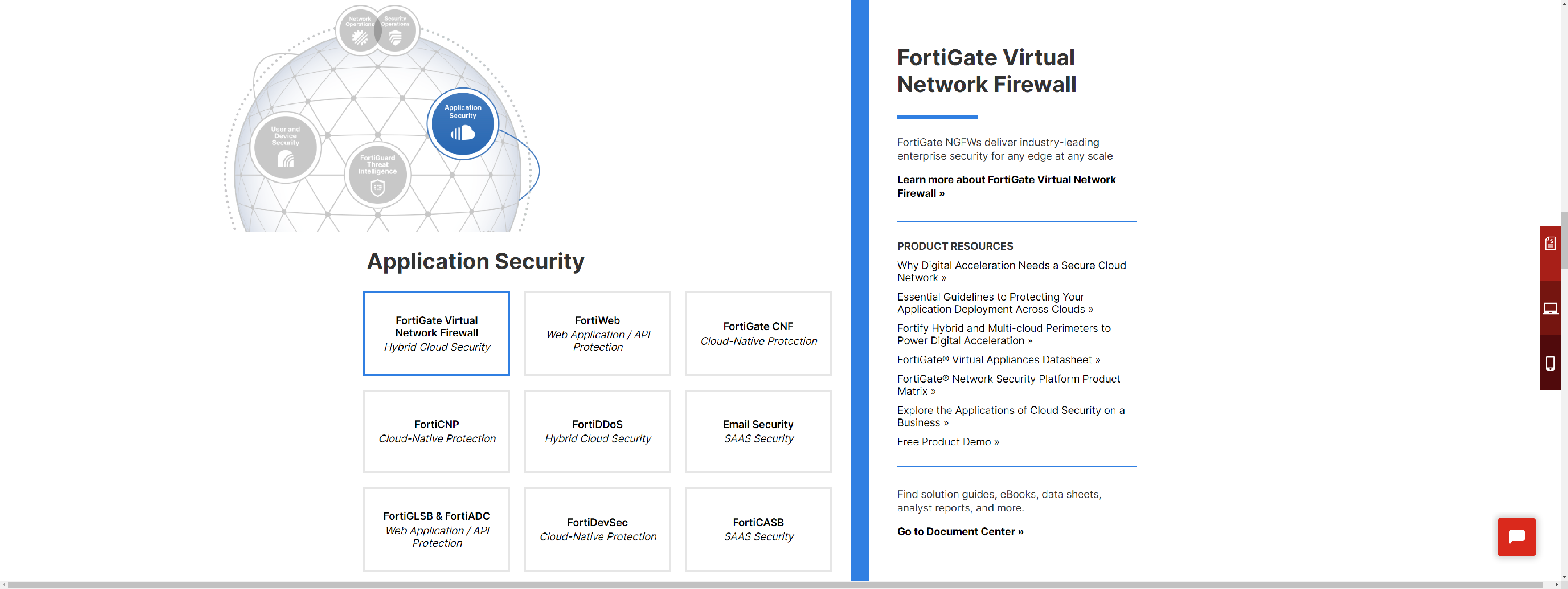
Fortinet Security Fabric delivers a rich set of application security solutions for protecting critical business applications.
- Applications Can Live Anywhere
- Edge Compute
- Deployment Complexity
- Forced Acceleration
- Cloud Threats
AIRIAM
Airiam works with your team and cloud provider to ensure your data is protected.
- Manage identities and access
- Manage vulnerabilities and cloud security posture
- Design for availability in the event of outages or when apps go down
- Plan and engineer for resilience
ZENTERA

Zentera’s software-based Zero Trust Fabric solutions enable application segmentation and secure access, within and across any network environment.
- Instant and secure access to all your machines
- Connect applications, not networks
- Protect critical applications
- Leverage our global network – or use yours
- Combating cyber fraud with Zentera Air Ultimate
CLOUD4C

Cloud4C delivers a frictionless transition of your entire IT environment on a cloud platform of choice.
- Datacenter Migration and Infrastructure Modernization
- Data Migration
- Enterprise Platforms Migrations
- Application Migration and Modernization
- Disaster Recovery and Enterprise Backup Services
- Cloud Monitoring and Reporting
- Cybersecurity on Cloud
- Hyperautomation and RPA
VERITIS
Veritis Cloud migration services, solutions & strategies can advise on the best migration approach (AWS, Azure, GCP, Oracle, IBM) for your enterprise in US.
- Accelerated Deployment
- Simplified Infrastructure
- Efficient Monitoring
- Improvised Security
- Zeroing-down Data Centers
- Investment-Winning Services
- Enhanced Key Metrics Logging
OPTIV

Optiv helps clients take a comprehensive approach to their cloud transformation.
- Build momentum
- Simplify your existing infrastructure
- Strategically leverage public cloud and native services
- Enable inherent security
ZAZMIC
Zazmic – migrate safely with no business disruptions, optimize your IT system costs, and scale seamlessly with the cloud.
- Reduced Expenses
- Higher Data Security
- Seamless Integration
- Increased Agility
- Cost Optimization
- No Business Disruptions
The main Cloud Migration Security best practices
1. Plan your migration: Develop a comprehensive migration strategy that includes security considerations from the beginning. Define your security goals and requirements to ensure a smooth transition.
2. Assess your current security posture: Conduct a thorough evaluation of your existing security controls and identify any vulnerabilities or weaknesses. This assessment will help you prioritize security measures during the migration process.
3. Encrypt data in transit and at rest: Implement strong encryption techniques to protect your data during migration and storage. Use secure communication protocols (like TLS) and encryption algorithms to safeguard data in transit, and encrypt data at rest using encryption keys managed by you.
4. Implement access controls and identity management: Utilize Identity and Access Management (IAM) tools to manage and control user access to your cloud resources. Enforce the principle of least privilege, granting only the necessary permissions to users and regularly review access privileges.
5. Secure your cloud environment: Employ security measures provided by your cloud service provider, such as firewalls, intrusion detection systems, and network security groups. Configure these services properly to ensure the highest level of protection.
6. Enable monitoring and logging: Implement robust logging and monitoring mechanisms to detect any suspicious activities or potential security breaches. Regularly review and analyze logs to identify any unauthorized access attempts or unusual behavior.
7. Conduct regular vulnerability assessments and penetration testing: Perform periodic security assessments to identify any vulnerabilities or weaknesses in your cloud environment. Conduct penetration tests to simulate real-world attacks and validate the effectiveness of your security measures.
8. Train and educate your staff: Provide adequate training to your employees on cloud security best practices. Make them aware of the risks associated with cloud migration and educate them on how to handle sensitive data securely.
9. Perform regular backups: Ensure you have proper backup mechanisms in place to recover data in case of any security incidents or data loss. Regularly test the restoration process to verify the integrity of your backups.
10. Stay up to date with security updates and patches: Keep your cloud environment and associated tools up to date with the latest security updates and patches provided by your cloud service provider. Regularly review the vendor notifications and apply necessary updates promptly.
By following these best practices, you can enhance the security of your cloud migration process and mitigate potential risks. Remember that security is an ongoing process, so it’s essential to regularly assess and improve your security measures as new threats emerge.