Endpoint detection and response (EDR) software is a security solution designed to detect and respond to advanced cyber threats that traditional anti-virus software is unable to identify. EDR software is commonly used by businesses to increase cybersecurity and defend their sensitive data against cyber attacks.
Discover the top 11 best Endpoint Detection and Response (EDR) Software Solutions
OPENEDR
EDR (Endpoint Detection and Response) has now become Open Source (OSS), providing EDR Security with a next gen Platform.
- Visibility and coverage: Open EDR® solutions provide visibility into all activity and can cover both physical and virtualized environments
- Detection: It provides an effective solution on detecting potential threats
- Response: It reacts quickly and helps you contain and remediate incidents
- Management and reporting: It is easy to manage and provide comprehensive reports that can help you improve your security posture
BITDEFENDER
Take EDR security to the next level with Bitdefender Endpoint Detection and Response. Advanced attack visibility and response for all endpoint security solutions.
- Advanced Risk Analytics
- Industry-Leading Threat Detection
- Cross-Endpoint Detection and Response
- Visualization at the Organization Level
- Streamlined Investigation and Response
- Time-Saving Reporting and Alerting
HEIMDALSECURITY
Heimdal Endpoint Detection and Response provides unique prevention, threat-hunting, and remediation capabilities, empowering you to quickly and effortlessly respond to sophisticated malware.
- All-encompassing security model
- Less stress, more productivity
- Greater visibility, faster response
KASPERSKY
Kaspersky Endpoint Detection and Response helps enterprises detect, investigate and respond to advanced security incidents more effectively using existing resources.
- IoC-based discovery
- IoA analysis empowered by MITRE ATT&CK mapping
- Automated threat intelligence — Kaspersky (Private) Security Network
- YARA rules (customizable by your IT security team)
- Sandbox analysis of suspicious objects
- Cloud ML for APK file analysis
- Digital certificate verification
- External threat intelligence cooperation
CHECKPOINT
Harmony Endpoint is a complete endpoint security solution that prevents the most imminent threats to the endpoint such as ransomware, phishing or malware.
- Complete Endpoint Protection
- Fastest Recovery
- Best Total Cost of Ownership
N-ABLE
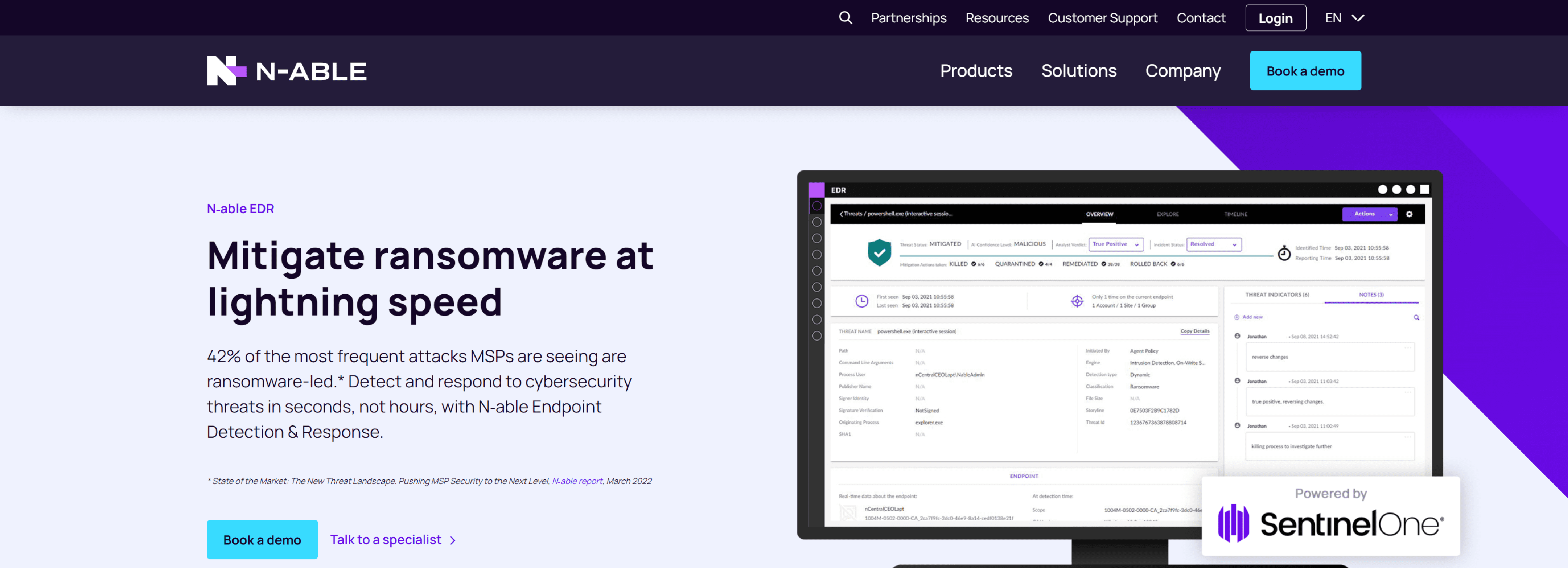
N-able Endpoint Detection and Response (EDR) helps MSPs identify and secure customer devices from the latest threats, including those antivirus can’t catch.
- Easily prove value to your customers
- Accelerate threat incident response
- Demonstrate safe business to insurers
- Elevate your business with dedicated resources
CYBEREASON
Cybereason AI-Driven XDR Platform provides predictive prevention, detection and response that is undefeated against modern ransomware and advanced attack techniques.
- Threat Intelligence
- Instant Remediation
- Detection Speed and Accuracy
- ML-Powered Detection and Correlation of Malicious Behaviors
- Proven Efficacy
SOPHOS
Respond remotely to security incidents on endpoints and servers with precision. Get 30 days of cloud storage and 90 days on-disk data retention with Sophos EDR.
- Cross reference indicators of comprise from multiple data sources to quickly identify, pinpoint and neutralize a threat
- Use ATP and IPS events from the firewall to investigate suspect hosts and identify unprotected devices across your estate
- Understand office network issues and which application is causing them
- Identify unmanaged, guest and IoT devices across your organization’s environment
DATTO
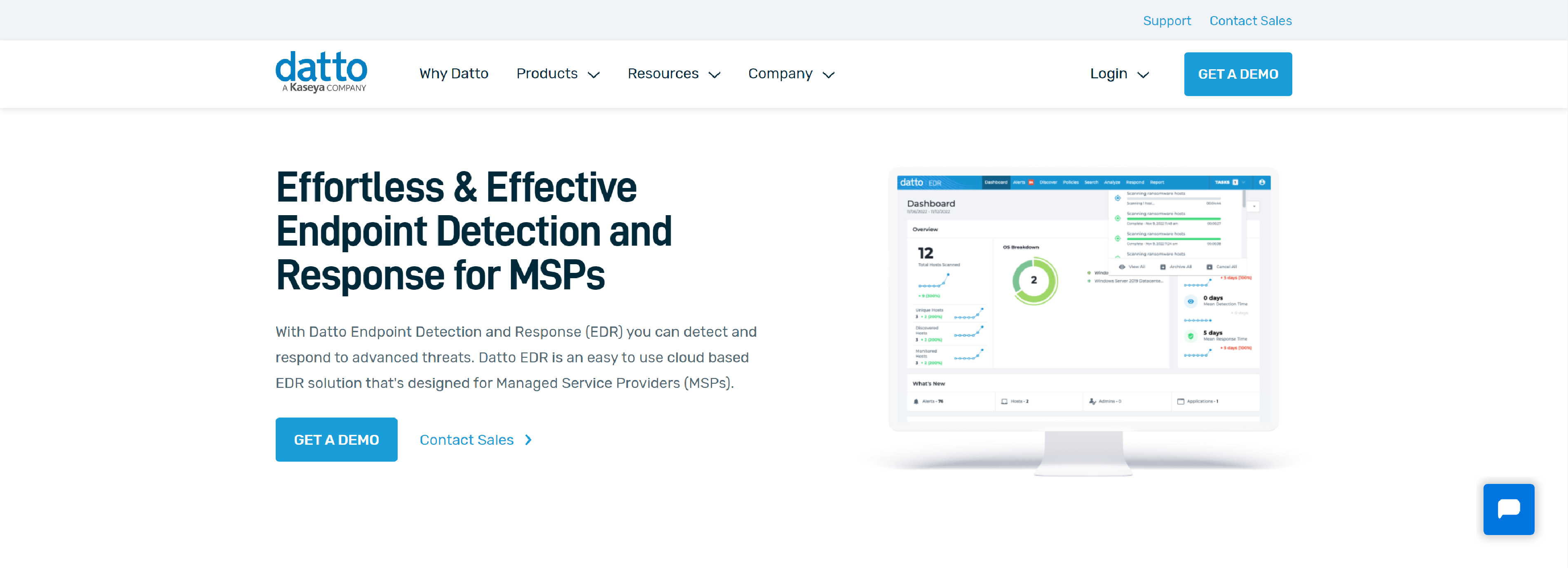
Effortlessly respond to advanced threats and protect your clients endpoint devices with Datto Endpoint Detection and Response.
- Click-to-respond
- Detect fileless attacks with behavioral analysis
- MITRE ATT&CK mapping
- Smart Recommendations
- Scalable remote response actions
- Integrated EDR and RMM
FORTINET
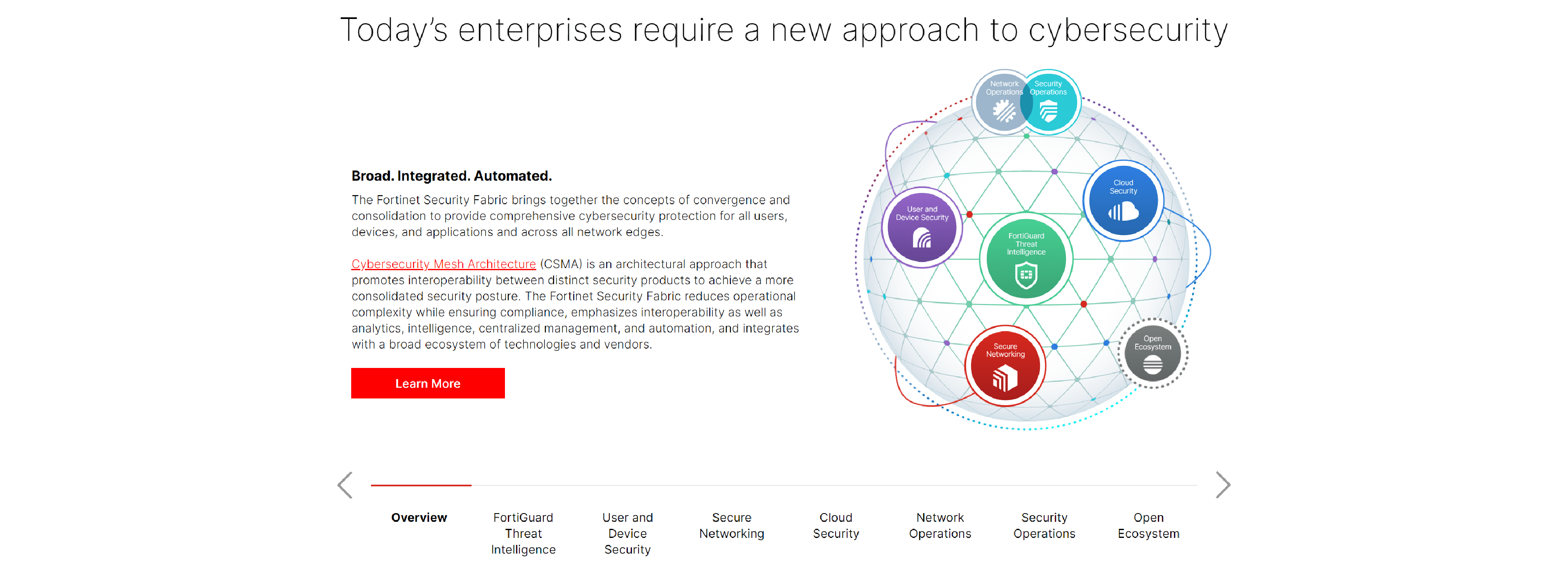
Fortinet delivers cybersecurity everywhere you need it. We secure the entire digital attack surface from devices, data, and apps and from data center to home office.
- Discover and control
- Detect and Defuse in Real Time
- Automatic Incident Response
- Instantly Stop Attacks
- Gain Efficient Security Operations
- Minimize Business Impact
WITHSECURE
WithSecure Elements Endpoint Detection and Response solution provides enhanced detection capabilities and security against cyber attacks and data breaches.
- Advanced response capabilities
- Broad Context Detection
- Event Search
- Elevate to WithSecure
- Automated Response
- Host isolation