If you run a business, especially one that deals with valuable information, you can never have too much security. There is a world of hackers trying to get into your system to steal information. With the dangers of hackers, there are also varmints such as spyware, viruses, spam mail and pop-ups trying to get into your computer network. Some of these intruders such as spam mail and pop-ups are simply bothersome while some can be destructive to your computers if you allow them in. In today’s world, there are also threats from inside your computer network, an area once viewed as safe. Like software that protects your computers from outside threats, network security software can cut down on threats that come from inside your own network.
As mentioned, network security comes in two varieties, internal and external. External means protecting you system from network security threats that come from any place other than inside you internal network or LAN. Internal security protects your system from intrusions on the network you own. An example would be an attack by one of your own employees.
There are several ways to handle the problem of computer network security. These all involve adding something to your network internally. If you decide to go the security software route there are several companies that offer solutions. Some companies only offer firewall protection. If you are only going to be running a web-server this may be the only protection you need. If you need to protect your personal computer, the one you use to keep tax and bank records on, surf the net, and open emails, you may want to consider an Internet security suite. There are many companies offer Internet security suite solutions to choose from. Make sure to pick one that will protect you system from viruses, spam, pop-ups, spyware, and hacker attacks with one program.
If you decide to go the hardware route for network security, then you will have to buy equipment that you must program and setup properly to work with your network. Just like software driven security, hardware security offers a wide range of protection. Also like software, hardware is customizable to your applications. However, hardware security platforms offer much more security than software, simply because these appliances stand alone and are not tied to the computer the hacker or virus might be trying to infect. This hardware simply gives hackers or viruses one extra layer of protection they would have to penetrate to gain access to your network. Obviously, a combination of hardware and software is the ultimate in network security, adding more layers or protection.
Whether you are using network security software or hardware on either an internal or external network, the goal is the same – an intruder free system with zero down time. Why? Because downtime means zero productivity and zero productivity means zero profit.
MANAGEENGINE
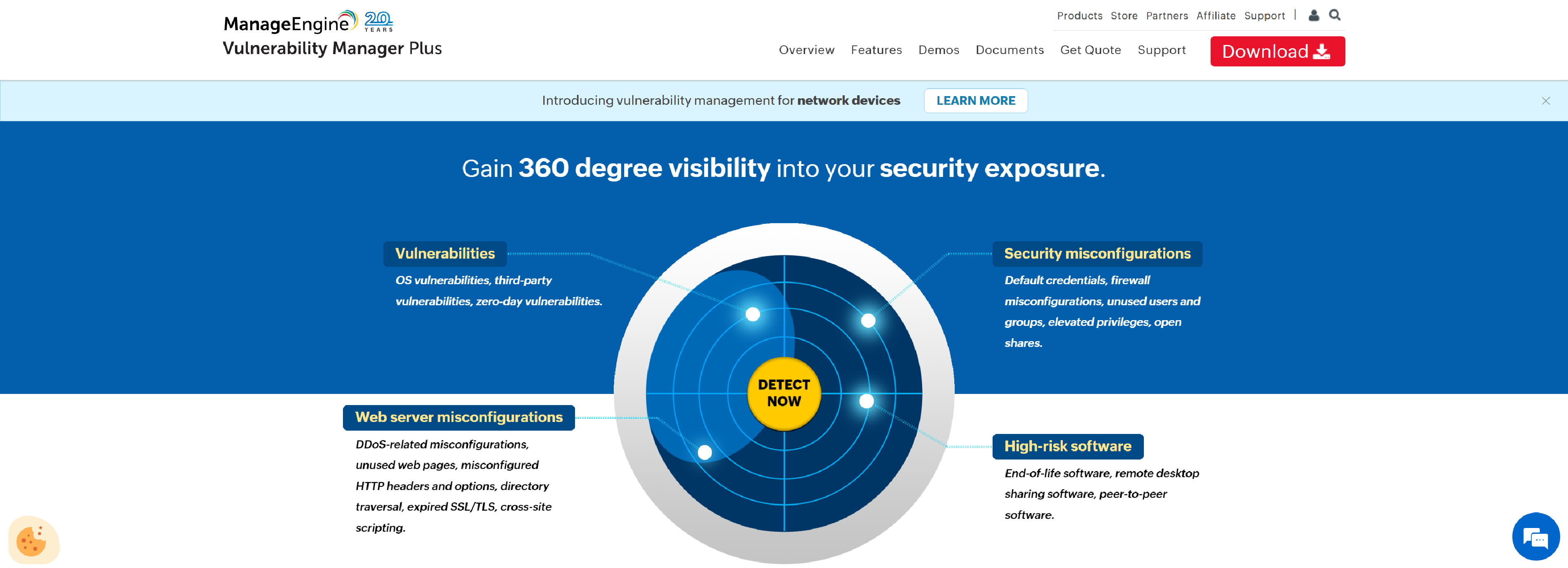
ManageEngine Vulnerability Manager Plus is a prioritization-focused threat and vulnerability management software for small-medium sized businesses offering comprehensive assessment of vulnerabilities and built-in patch management.
Vulnerability Manager Plus offers a plethora of security features such as security configuration management, automated patching module, high-risk software audit, web server hardening, and many more to secure your network from being breached.
Advantages:
- Improve your security posture with exclusive threat and vulnerability management.
- Instant detection and mitigation of misconfigurations in your enterprise network.
- Automate patch management end-to-end.
- Achieve compliance with CIS benchmarks.
- Gain Insights with interactive dashboards and intuitive reports.
FIREMON
The FireMon Firewall Management Software allows you to continuously analyze, visualize and improve your existing firewall & network security infrastructure.
- Security Manager
- Global Policy Controller
- Policy Planner
- Policy Optimizer
- Lumeta
- Risk Analyzer
- Immediate Insight
SKYBOXSECURITY
Integrated security management solutions for enterprise–scale vulnerability and threat management, security policy and firewall management.
- Gain the advantage over attackers with advanced vulnerability and threat intelligence
- Zoom in on security control gaps with comprehensive network modeling and cutting-edge attack vector analytics
- Protect important systems and data in minutes with remediation plans right for your network and its threats
TUFIN
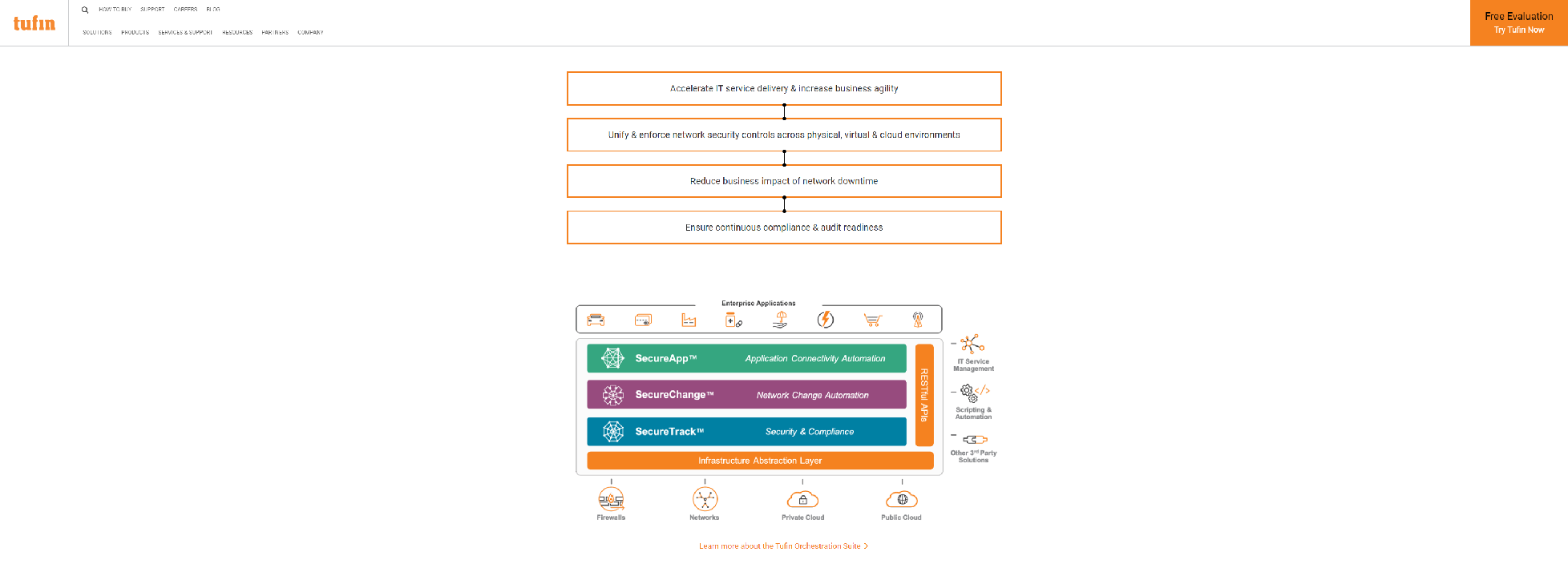
Tufin allows more than 2,000 enterprises to streamline the management of security policies across complex, heterogeneous environments. Tufin uses policy-based automation to boost security and increase agility for the world’s largest organizations and most complex networks.
- Unified Security Policy
- Compliance & Audit Readiness
- Network Security Change Automation
- Digital Business Continuity & Agility
- Cloud Security
- Multi-Vendor Support
FIREEYE
FireEye offers a single platform that blends innovative security technologies, nation-state grade threat intelligence, and world-renowned Mandiant consulting.
- Enterprise Security
- Mandiant Consulting
- Managed Defense
- Threat Intelligence
PALOALTONETWORKS
Palo Alto Networks enables your team to prevent successful cyberattacks with an automated approach that delivers consistent security across cloud, network and mobile.
Cloud security:
- Public Cloud
- SaaS
- Branch & Retail
- Mobile Users
Enterprise:
- Next-Generation Firewall
- Threat Prevention Services
- Endpoint Protection
- 5G / IoT
GLASSWIRE
GlassWire is a modern personal firewall and network monitor with over 13 million downloads.
- Keep track of your data usage on your PC or mobile phone and get alerted before going over data limits
- Go back in time with GlassWire’s network time machine to see what your PC was doing while you were away
- Get alerted every time a new app accesses the network, and block it if necessary
- See detailed network usage statistics broken down by IP/Host, app, network traffic types, and more
CHECKPOINT

Check Point Infinity architecture delivers consolidated Gen V cyber security across networks, cloud, and mobile environments.
- Network Security
- Cloud Security
- Mobile Security
- Endpoint Security
- Security Management
- Infinity Total Protection
ALIENVAULT
At AlienVault our mission is to enable all organizations to detect and respond to today’s threats in cloud, on-premises and hybrid cloud environments.
- Know Your Assets & Vulnerabilities
- Detect Threats & Intrusions Faster
- Analyze Security Incidents with SIEM
- Stay Vigilant with Continuous Threat Intelligence
NETFORT
NetFort LANGuardian is a network visibility solution which uses deep packet inspection to monitor, troubleshoot, and report on user & network activity.
- Tracking the source of Ransomware
- Detecting source of malware such as Conficker
- Investigating reports of suspect traffic (both in and out)
- Investigating and cleaning up after phishing emails
- Alerting on spoofed DNS traffic
- Dealing with external organizations reported malware originating from your network
- Inspect outgoing traffic from your network
- Find the source of SPAM originating from network
- Track down individual users downloading large volumes of data from internal shares
- Report on mobile device activity by MAC address
SOLARWINDS
SolarWinds IT monitoring and management tools are built for SysAdmins and network engineers who need powerful and affordable tools. Get a free trial today.
- Automated threat intelligence updates
- Prioritized responses reduce risks
- Detect threats everywhere
- Demonstrate compliance for PCI DSS, SOX, and more
PAESSLER
PRTG monitors your whole IT infrastructure 24/7 and alerts you to problems before users even notice. Find out more about the monitoring software that helps system administrators work smarter, faster, better.
Advantages:
- A constant eye on software and hardware
- Prompt, customizable alarm
- Historical data for comparison
- Compatibility with all the big manufacturers
- APIs for individual customization
- A centralized monitoring solution