An intrusion detection software is a software that helps you monitor your system and/or network for policy violations or any other malicious activity. If any are detected, the intrusion detection software will report back to you, giving you a number of solutions to handle the situation. After the detection is made the software will try to stop the possible incidents or, if that is not possible, to isolate the problem so it wouldn’t cause any additional damage to your system and network.
The primary use of the intrusion detection software is to detect any possible events that will affect your system’s well being, to record all the information available, to try to stop them and to notify the system administrators about the incidents. Also, intrusion detection software is used by large companies and organizations for purposes like recognizing problems with security policies, stopping people from breaking the security policies or documenting about possible threats. Nowadays, with the progress made by technology, nearly every company or organization is required to use the intrusion detection software in order to keep their private valuable information safe from outside attackers.
Using the intrusion detection software will not require any special skills, but if you don’t know a lot about computers it is always best to notify the person responsible with the administration. In case a detection is made, the software will inform you about it and will specify the type of activity detected. The terminology used by the intrusion detection software is simple and easy to use if you have a bit of a knowledge about computers.
Here are some examples:
- Alert – reports that the system in under attack
- True Positive – an attack that produces an alarm
- True Negative – no attack has occurred and no alarm is triggered
- False Positive – an event triggering an alarm when no attack was produced
- False Negative – an attack not being detected
- Site Policy – a set of regulations that will guide an intrusion detection software’s functioning
The intrusion detection software, like any other software, has some limitations, as the technology advance is very fast and every day new methods to trick the system are discovered. One of the main weaknesses is the high false alarm rate. Many things can generate a false alarm, from software bugs to Internet packets not being read and it is never pleasant to look for a problem where there is none. Another problem is keeping the software up to date. If you are not familiar with the term, you might be in danger. Many attacks target outdated versions of the intrusion detection software, so it is always important to keep it updated. If you don’t know how, ask for help. You can never be to careful about it.
In conclusion, it is always important to use an intrusion detection software in order to secure the privacy of your information. Whether you are a domestic user or part of a larger organization, the risks are the same. People are always trying to access private information and the intrusion detection software is a useful tool that helps you keep them away.
ManageEngine Firewall Analyzer
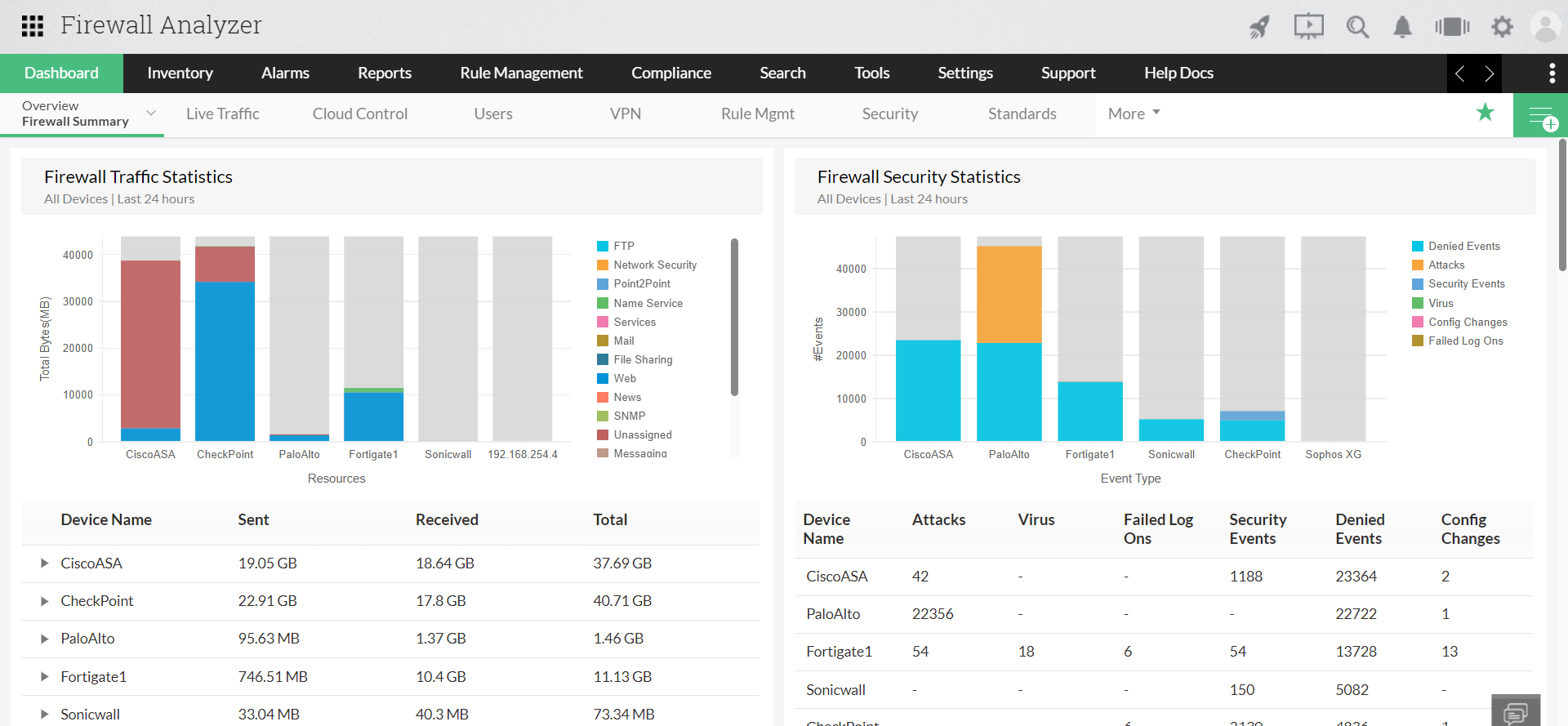
ManageEngine Firewall Analyzer is log analytics, firewall optimization, and configuration management software for network security devices.
- Centralized firewall log management
- Automated security and compliance reporting
- Bandwidth monitoring and traffic analysis
- Firewall policy management and refinement
- Threat intelligence and event correlation
- Built-in IDS and IPS monitoring
SECUCLOUD
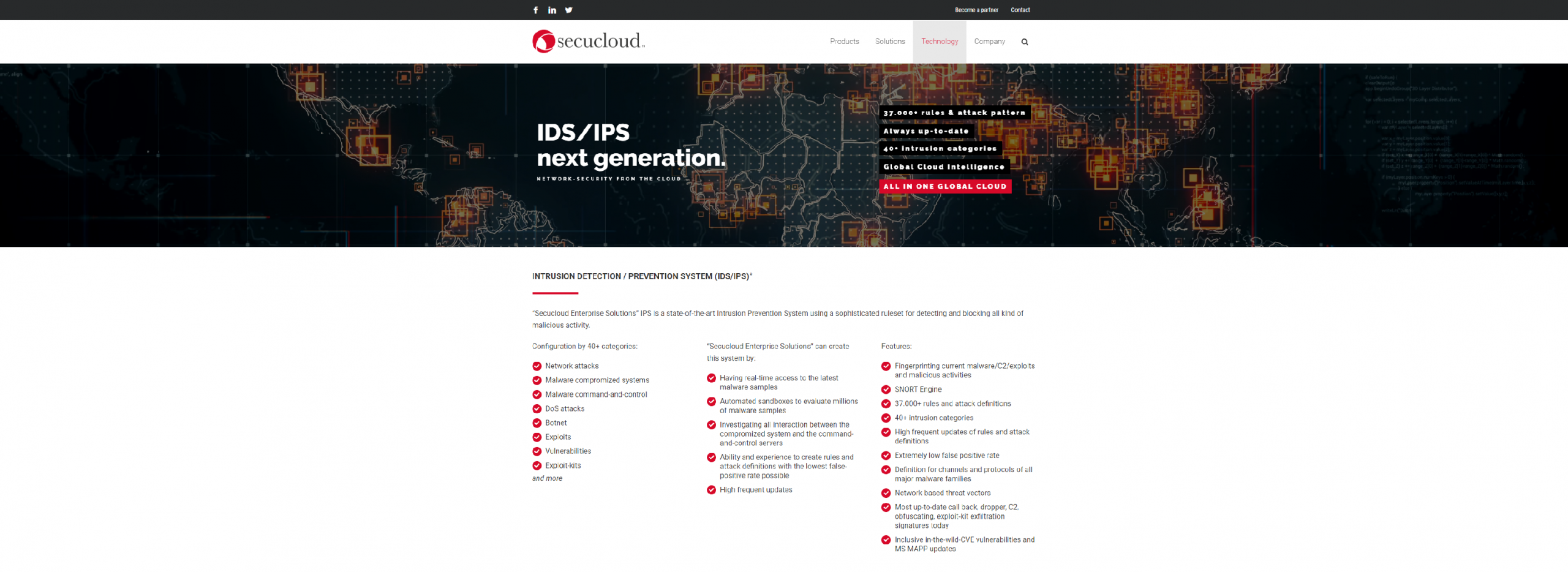
Secucloud Enterprise Solutions IPS is a state-of-the-art Intrusion Prevention System using a sophisticated ruleset for detecting and blocking all kind of malicious activity.
- Fingerprinting current malware/C2/exploits and malicious activities
- SNORT Engine
- 37.000+ rules and attack definitions
- 40+ intrusion categories
- High frequent updates of rules and attack definitions
- Extremely low false positive rate
- Definition for channels and protocols of all major malware families
- Network-based threat vectors
- Most up-to-date call back, dropper, C2, obfuscating, exploit-kit exfiltration signatures today
- Inclusive in-the-wild-CVE vulnerabilities and MS MAPP updates
ALERTLOGIC

Alert Logic seamlessly connects an award-winning security platform, cutting-edge threat intelligence, and expert defenders – to provide the best security and peace of mind for businesses 24/7, regardless of their size or technology environment
- Pre-built automated deployment capabilities get you up and running quickly – start monitoring security threats in just minutes
- Low-impact agents self-configure upon deployment and self-register/deregister for no-touch support of auto-scaling
- Deployed agents encrypt and transmit your ingress, egress, and lateral network traffic to the Alert Logic backend for processing
- We compare your network traffic with over 17,000 active IDS signatures that detect a wide array of attack methods, including exploits in web app frameworks, app stack components, and attack methods included in the OWASP Top 10
- 24/7 security monitoring, expert incident analysis and live notifications of critical attacks by security analysts in our global SOCs
SECURITYONION
Security Onion is a free and open source Linux distribution for intrusion detection, enterprise security monitoring, and log management.
- HIDS alerts from Wazuh and NIDS alerts from Snort/Suricata
- Asset Data from Bro
- Full packet capture from netsniff-ng
- Host data via Beats, Wazuh, syslog, and more
- Session data from Bro
- http/ftp/dns/ssl/other logs from Bro
SOLARWINDS
Improve your security posture with an easy-to-use, affordable SIEM tool – SolarWinds Security Event Manager (formerly Log & Event Manager).
- Centralized log collection and normalization
- Automated threat detection and response
- Integrated compliance reporting tools
- Intuitive dashboard and user interface
- Built-in file integrity monitoring
- Simple and affordable licensing
OSSEC
OSSEC is a multiplatform, open source and free Host Intrusion Detection System (HIDS). You can tailor OSSEC for your security needs through its extensive configuration options, adding custom alert rules and writing scripts.
- OSSEC is fully open source and free
- OSSEC offers comprehensive host-based intrusion detection across multiple platforms including Linux, Solaris, AIX, HP-UX, BSD, Windows, Mac and VMware ESX
- OSSEC helps organizations meet specific compliance requirements such as PCI DSS
SURICATA-IDS
Suricata is a free and open source, mature, fast and robust network threat detection engine. The Suricata engine is capable of real time intrusion detection (IDS), inline intrusion prevention (IPS), network security monitoring (NSM) and offline pcap processing.
- IDS / IPS
- High Performance
- Automatic protocol detection
- NSM: More than an IDS
- Lua scripting
- Industry standard outputs
ZEEK
Zeek is a powerful network analysis framework that is much different from the typical IDS you may know.
- Adaptable
- In-depth Analysis
- Efficient
- Highly Stateful
- Flexible
- Open Interfaces
- Forensics
- Open Source