Defending web applications from hackers is an essential task of every online business. Critical business applications that contain sensitive data about business processes and customers are at risk from hackers and malicious viruses. Cost effective security measures need to be taken which may entail moving away from proprietary client/server applications to web applications that are not only cost effective but provide a highly extensive delivery platform. The impact of an attack on websites can cause costly and embarrassing disruptions in a company’s services. Without proper web security testing measures, businesses like eBay can be severely affected for indefinite periods causing a great loss of business and the trust of millions of users. Besides, the risk of stolen data is always imminent.
Web security testing measures need to protect web applications with a minimal or no impact on operations or changes in system architectures. Without testing many online application vulnerabilities may be overlooked. Every web application relies on a variety of software components which includes the operating system, web server, databases and more. These vulnerabilities are considered in web application security testing.
Vulnerabilities will be found regularly, requiring the need for patches to manage application security. Patch management is a complex issue that requires a proactive IT team to handle the deployment of urgent patches which could disrupt normal operations. No matter how efficient a patching process is, there is no guarantee of protection from attacks. Hackers use a number of techniques such as SQL injection, cross site scripting, buffer overflow, and denial of service. A large number of attacks make use of vulnerabilities rather than configuration issues. For the most part, hackers find ways to exploit vulnerabilities faster than they could be patched, which can only be solved through a remote online web application security-testing service.
A web security testing service will ensure that a company is fully compliant with rules and regulations, and is able to respond quickly to any attacks. Such as service is able to locate vulnerabilities from a hacker’s view point and address the needs accordingly. A web application security scan will reveal vulnerability to SQL injection, installation path disclosure, command execution, .Net exception, PHP code injection, script language error, URL redirection, remote, file inclusion, cookie manipulation, and more. It will also test vulnerabilities for website components such as web servers, web server technologies, HTTP methods, backup files, directory indexing, directory permissions, third party applications, and more.
MANAGEENGINE
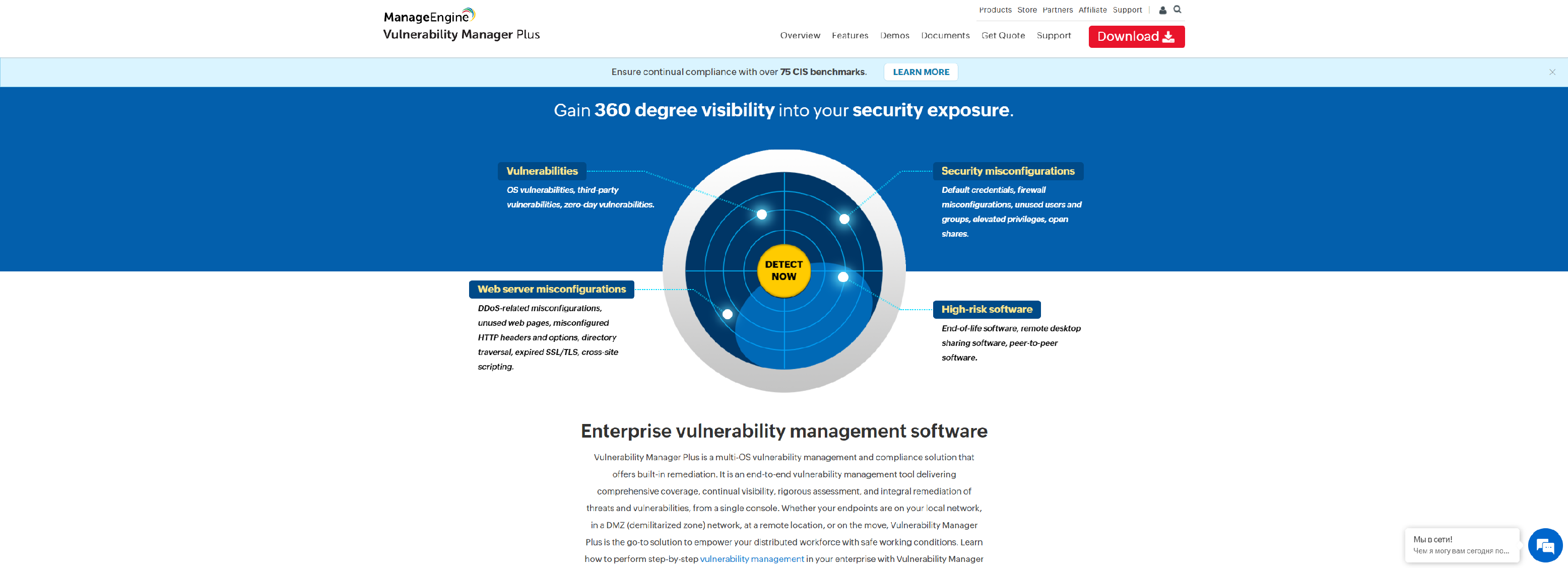
Vulnerability Manager Plus is a prioritization-focused vulnerability management tool that helps you manage vulnerabilities from a centralized console & offers built-in patching.
- Vulnerability assessment
- Compliance
- Patch management
- Security configuration management
- Web server hardening
- High-risk software audit
- Zero-day vulnerability mitigation
QUALYS
Qualys, Inc. helps your business automate the full spectrum of auditing, compliance and protection of your IT systems and web applications.
- Find and catalog all your web apps
- Perform deep, exhaustive application scans at scale
- Visualize and document your web app security status with actionable data
- Rapidly harden web apps with integrated WAF
ARACHNI-SCANNER
Arachni is a Free/Public-Source Web Application Security Scanner aimed towards helping users evaluate the security of web applications.
- Free/Public Source Software
- Multiple deployment options
- Abundance of security checks
- Integrated browser environment
- Intelligent, on-the-fly adaptation to each web application
- Mobile ready – in more ways than one
- High performance
- Highly detailed, well-structured reports
SUBGRAPH
Vega is a free and open source web security scanner and web security testing platform to test the security of web applications.
- Vega has a well-designed graphical user-interface
- Vega is written in Java and runs on Linux, OS X, and Windows
- Vega detection modules are written in Javascript. It is easy to create new attack modules using the rich API exposed by Vega
VEGABIRD (VOOKI)
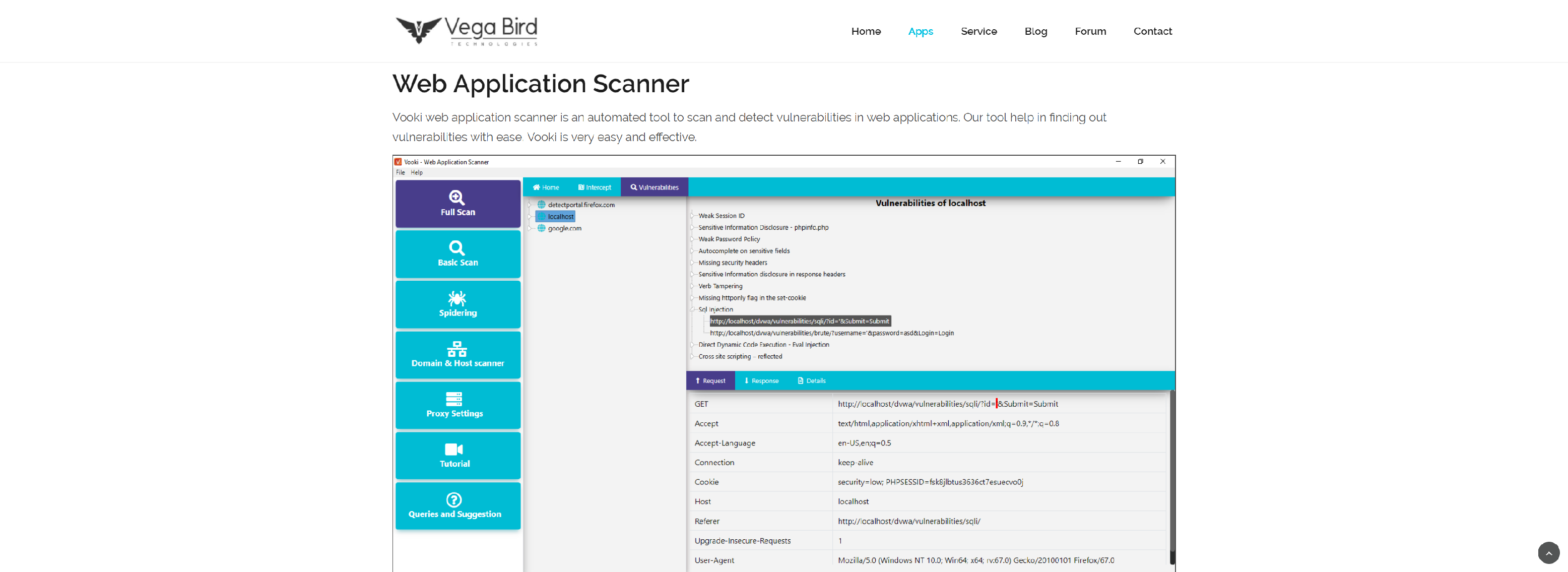
Audit your web security with Vooki. It is a free web application vulnerability scanner which gives us a perfect scan report about the scanned networks, applications.
- SQL Injection.
- Command Injection.
- Header Injection.
- Cross-site scripting – reflected.
- Cross-site scripting – stored.
- Cross-site scripting – dom based.
- Missing security headers.
- Malicious JS script execution.
- Using components with known vulnerabilities.
- Jquery Vulnerabilities.
- Angularjs Vulnerabilities.
- Bootstrap Vulnerabilities.
- Sensitive Information disclosure in response headers.
- Sensitive Information disclosure in error messages.
- Missing Server Side Validation.
- Javascript Dynamic Code Execution.
- Sensitive Data Exposure
PROBELY
Probe automates vulnerability scanning in a cost-effective, sleek and intuitive web interface.
- Probely integrates with popular tools such as Slack and JIRA
- Anything that can be done using the Web App can also be done directly via the API
- Onboard your team and assign vulnerabilities to team members
- Scan your production environment with non-intrusive scans, and your testing with intrusive and complete scans
- Archive PDF reports periodically as an evidence that you are serious about Security
- Probely’s spider was developed from scratch to navigate rich Javascript apps, just like a normal browser
TENABLE
Detect more vulnerabilities with Tenable Web Application Scanning.
- Reduce administration costs
- Increase accuracy of security testing
- Reduce product sprawl and improve visibility
HACKMETRIX
Hackmetrix is a web security scanner that allows developers to easily run tests on their web applications. It’s built in collaboration with ethical hackers, and scans for hundreds of vulnerabilities, including cross-site scripting (XSS) and SQL injections.
- Schedule recurring scans and get notified with the results monthly
- Use our API to integrate security scans into your development workflow
- Connect with Slack to get notifications where your team already is
- Export your results in CSV, JSON or XML to import into other services or make your own reports
The Importance of Security Testing For Web Based Applications
It is essential to guarantee that a website is free from vulnerabilities, which could otherwise have a negative impact on visitors as well as the integrity of the website owner.
The tightest security features can only be in place through web security testing. Many developers refer to internet security testing as penetration testing. This involves the evaluation of security measures related to a website or web application. This enables developers to find security flaws that may arise from the implementation process. Security tests enable designers and developers to collaborate about any vulnerability issues of a website or web based application, and generates solutions to correct errors and prevent further flaws. Moreover, it also ensures that the output is of the highest quality for end users.
Web security testing prevents any external modifications from being made to a website’s settings. It can identify errors immediately prior to the release of a website and avoid the occurrence of major security concerns. Security testing includes tests on servers, firewalls, routers, operating systems, and more. Testing begins with checks on information on data accessible to website views followed by a network enumeration. This involves the testing of open ports, hosts, and security vulnerabilities that provide access to the control panel of the website.
Web security checks are essential to develop. These checks may mean a slower response time by the network during scanning, but are integral to the security of any web application system. It is important to have certified testers on the job in order to minimize any risks. One of the most popular methods of analyzing the security of a computer system is the penetration test. This involves simulating an attack during which an analysis of the system is performed for any weaknesses and vulnerabilities. These checks are conducted in different ways which includes white box, black box and grey box testing.
White box security examinations are of a higher order than black box security checks. Testers without knowledge of the system and its resources adopt black box testing where their first task is to locate the system and look for its extent. White box testing is conducted when testers have information such as IP addressing, source code, and network diagrams. Many are of the opinion that black box testing method is the best. Whatever web security examination method is adopted, it requires a thorough understanding of the backend of all applications.