A penetration test, or the short form pen test, is a “ethical” attack on an Information System with the intention of finding security weaknesses, potentially gaining access to it, its functionality and data. Penetration testing is not simply checking for un-patched systems with an automated scanning tool, that is a vulnerability scan. This is a test of the security posture, and capabilities of the target organization’s cyber security team.
Below are some benchmarks to meet while testing.
- The ability for the target to detect and respond to information gathering
- The ability for the target to detect and respond to footprinting
- The ability for the target to detect and respond to scanning and vulnerability analysis
- The ability for the target to detect and respond to infiltration (attacks)
- The ability for the target to detect and respond to data aggregation
- The ability for the target to detect and respond to data ex-filtration
Penetration testing should be goal oriented, you’re testing to identify specific vulnerabilities that lead to a compromise of the business or mission objectives of the target.
Penetration testing is about identifying risk that will adversely impact your organization.
The primary goal should be based around the impact to the target organization if you were compromised. Not compliance this would be a secondary goal.
Compliance does not equal secure. Target, Home-Depot, Jimmy Johns, Sony Pictures, [INSERT_NEW_VICTOM_HERE]… The list just keeps growing. You don’t want organization on this list.
For best results, you should test from all angles, not just the typical “from the Internet only”. For some reason a handful of clients always want a pen test “from the outside only”. They mainly think the threat is only going come from the Internet, and they think that this is the only way in from “outside”. What about your lobby IP phone with the extra switch port just waiting for someone to connect to. As an attacker, why would I waist time trying get in through the firewall if your back door is wide open. Most attacks come from within, disgruntled employee, guest on the network, or even the college intern that does nothing but social media all day. Not only from malicious users on the inside, even the best intentioned employee may bring their personal laptop in to use on lunch break and who knows what type of worm this person may have on a non-company asset. So if a test is done from the inside, and all discovered vulnerabilities from the inside are mitigated (all will never be mitigated) it’s going to make it that much harder directly from the Internet. Don’t be crunchy on the outside and all gooey on the inside. A Defense in Depth approach is always the best approach.
NETSPARKER
Netsparker is a single platform for all your web application security needs. Our web app security solution helps businesses of any size and industry identify vulnerabilities and prioritize fixes.
- Proof-Based Scanning
- Identify Your Vulnerabilities
- Detailed Vulnerability Information
- Built-In Assessment Tools
- Scale Your Security
- Scan All Your Web Assets
- Integrations
- Collaboration and Communication
- Automate Vulnerability Processing
- WAF Integration
- Dashboards and Reports
- Identify Your Technologies
- World-Class Support
ACUNETIX
Acunetix is an end-to-end web security scanner that offers a 360 view of an organization’s security. Allowing you to take control of the security of all you web applications, web services, and APIs to ensure long-term protection.
- Vulnerability Scanner – Automate Penetration Testing
- Highest Detection Rate – Highest SQL Injection and XSS Detection Rate
- Lowest False Positives – Interactive Application Security Testing (IAST) with AcuSensor
INTRUDER
Intruder is a cloud-based vulnerability scanner that finds cyber security weaknesses in your most exposed systems, to avoid costly data breaches.
- Automated Penetration testing
- Cloud Vulnerability Scanner
- Network Vulnerability Scanner
- External Vulnerability Scanner
- Internal Vulnerability Scanner
- Continuous Vulnerability Scanning
- Vulnerability Assessment Software
- A Modern Vulnerability Scanning Service
IMMUNIWEB

ImmuniWeb AI Platform for Application Security Testing, Attack Surface Management & Dark Web Monitoring.
- Money-Back Guarantee for a single false-positive
- Once your code is changed, our experts will promptly test it
- Business logic testing, SANS Top 25, PCI DSS & OWASP coverage
- Tailored remediation guidelines and 24/7 support
- One-click WAF virtual patching, SDLC & CI/CD integration
VERACODE
A simpler and more scalable way to increase the resiliency of your global application infrastructure, without slowing innovation.
- No AppSec Silver Bullet
- Beyond Automated Testing
- Comprehensive Results
- All Results In One Place
- Meet Compliance Requirements
- Test Entire Pipeline
BREACHLOCK
BreachLock platform leverages cerified hackers and AI-powered vulnerability scans to deliver a continuous and on-demand Penetration Testing as a Service.
- Automate Your Web Security Scanning
- Run On-Demand and scheduled scans
- Configure your scanning profile
- Run Authenticated Scans
- Scan single page applications
- Run API security scanning
- False Positive proof scanning
- Integrate with DeVops pipeline
- Retest your patches with a click
PORTSWIGGER
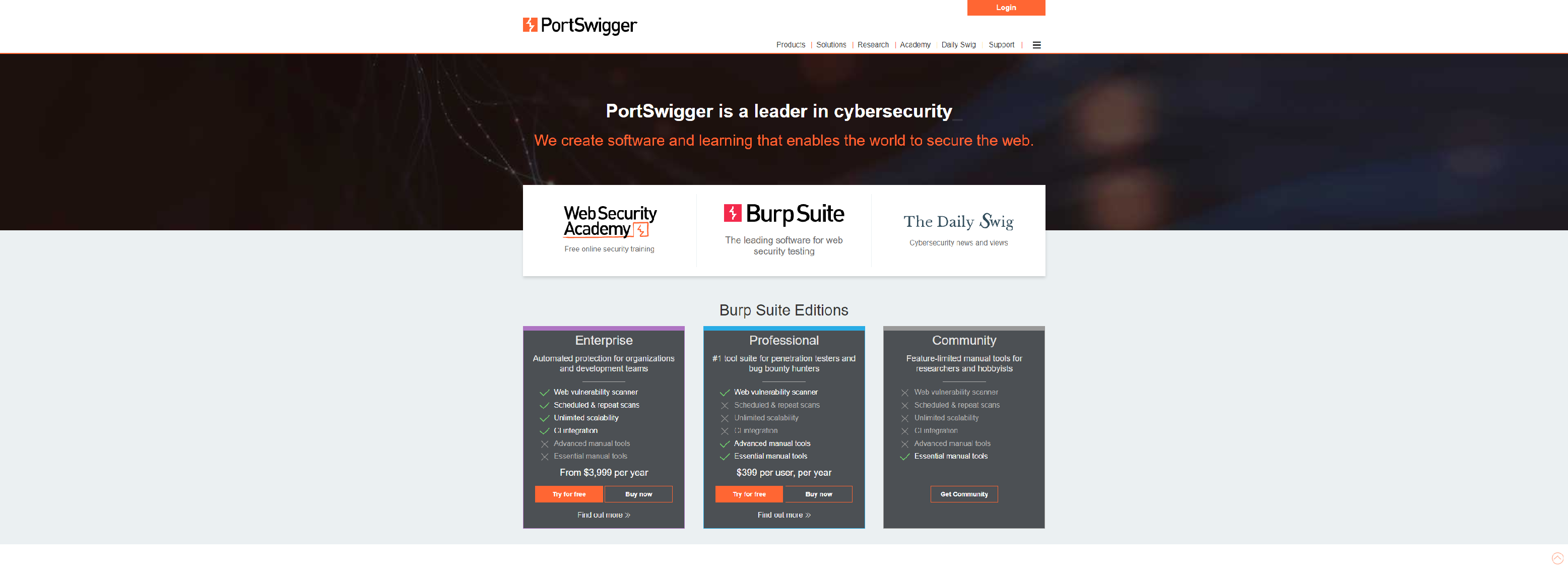
PortSwigger offers tools for web application security, testing & scanning.
- Web vulnerability scanner
- Scheduled and repeat scans
- Unlimited scalability
- CI integration
- Advanced manual tools
- Essential manual tools
BEYONDTRUST
Reduce risk with cross-platform vulnerability assessment and remediation, including built-in configuration compliance, patch management and compliance reporting.
- Retina CS (RCS)
- Retina Network Security Scanner (RNSS)
- Retina Host Security Scanner (RHSS)
- Retina Standalone Security Scanner (RSSS)
- BeyondTrust Network Security Scanner (BNSS)
- BeyondTrust Enterprise Vulnerability Management (EVM)
- BeyondTrust Host Security Scanner (BHSS)