SOC 2 (Service Organization Control 2) compliance audit is an assessment conducted to determine if an organization’s systems, processes, and controls comply with the Trust Services Criteria (TSC). The TSC is a set of principles and criteria developed by the American Institute of Certified Public Accountants (AICPA) to evaluate an organization’s controls over security, availability, processing integrity, confidentiality, and privacy.
A SOC 2 compliance audit is typically performed by a third-party auditing firm, also known as a Service Organization Control (SOC) auditor. The auditor evaluates the organization’s controls and processes to determine if they meet the requirements set out in the TSC. This helps provide assurance to clients, customers, and other stakeholders that the organization has appropriate measures in place to protect their data and ensure the availability and integrity of their services.
The SOC 2 compliance audit consists of two main types of reports: Type 1 and Type 2. Type 1 focuses on the design of the controls and determines if they are suitably designed to achieve the specified control objectives. Type 2, on the other hand, not only examines the design of the controls but also validates their effectiveness over a specified period (usually six months to a year). Type 2 provides more comprehensive and reliable information about the controls’ operational effectiveness.
The SOC 2 compliance audit process includes several steps. First, the organization and the auditor agree upon the scope and objectives of the audit. Next, the auditor assesses the organization’s control environment and identifies any potential risks. The auditor then evaluates the design and implementation of controls, including the organization’s policies, procedures, and documentation. This involves reviewing relevant documentation, conducting interviews with key personnel, and performing sample testing.
During the audit, the auditor focuses on the five relevant Trust Services Categories: Security, Availability, Processing Integrity, Confidentiality, and Privacy. Each category has specific criteria that an organization must meet to demonstrate compliance. For example, to meet the security criteria, the organization may need to demonstrate controls such as firewalls, access controls, and intrusion detection systems.
Once the audit is complete, the auditor issues a report summarizing their findings. This report includes a description of the organization’s controls, an evaluation of their design and operating effectiveness, and any identified gaps or deficiencies. The report also provides an opinion on the organization’s compliance with the TSC.
Achieving SOC 2 compliance is an essential requirement for many organizations, especially those that handle sensitive data or provide services to other companies. It demonstrates a commitment to maintaining strict controls and safeguards to protect client information. SOC 2 compliance audits provide valuable assurances to clients, as they can trust that the organization has undergone a rigorous evaluation to ensure the security, availability, processing integrity, confidentiality, and privacy of their data.
SOC 2 compliance audit is a comprehensive evaluation performed by a third-party auditor to assess an organization’s systems, processes, and controls according to the Trust Services Criteria. This audit helps organizations demonstrate their commitment to data security and regulatory compliance, providing assurance to clients and stakeholders.
SPRINTO
Sprinto is the #1 SOC 2 Automation Software that streamline and automates your SOC 2 certification and shortern your Journey.
- 1:1 guided implementation with compliance experts
- Baked-in MDM for entity health checks
- Centralized compliance + audit dashboard
- Ready-to-use system description and policy templates
- Built-in, flexible security training modules for SOC2
- Status history, tiered alerts, and streamlined workflows for SOC2 checks
DRATA
Drata automates the SOC 2 process so you can close deals faster, drive revenue, and build customer trust through continuous monitoring and assurance.
- Security Training
- Policy Center
- Support and Live Chat
- Continuous Control Monitoring
- Risk Assessment
- Vendor Management
- Real-Time Security Reports
- Endpoint Monitoring
- Control Library
SECUREFRAME
Secureframe streamlines the SOC 2 process at every step of the way. Get SOC 2 compliance within weeks with powerful security that seamless and easy-to-use.
- Meet your dedicated account manager
- Create your compliance policies
- Assess and manage vendor risk
- Complete a SOC 2 audit
- Scan and secure your cloud infrastructure
- Easily train personnel on security and privacy requirements
- Complete Secureframe SOC 2 readiness assessment
- Continually maintain SOC 2 compliance
TUGBOATLOGIC

Tugboat Logic – takes the misery and mystery out of passing security audits like SOC 2, PCI, and ISO 27001 so you can slay more deals and stay secure.
- Continuous monitoring of security controls
- Vendor-security questionnaires
- Mapped security controls
- Auto-answer RFP management
VANTA
Get ready for a SOC 2 audit in weeks instead of months with Vanta’s automated compliance software.
- Continuous monitoring
- Integrations
- Policies
- Documents
- Notifications
- Controls
- Employee management
- Risk assessments
- Vulnerability management
- Access reviews
- Inventory management
- Vendor reviews
- Remediation workflows
- APIs
- Smart system description
- Reporting
- Scoping
- Auditor portal
LOGICGATE
Risk Cloud’s SOC 2 (LogicGate) Compliance Application allows organizations to evaluate their internal controls, policies, and procedures against AICPA’s five Trust Services Criteria and helps them prepare for a SOC 2 attestation report.
- Link and Document SOC 2 Trust Services Criteria to Your Internal Controls from One Platform
- Improve Collaboration and Save Time with Automated Workflows
- Avoid Compliance Gaps and Effectively Implement Corrective Actions
JUPITERONE
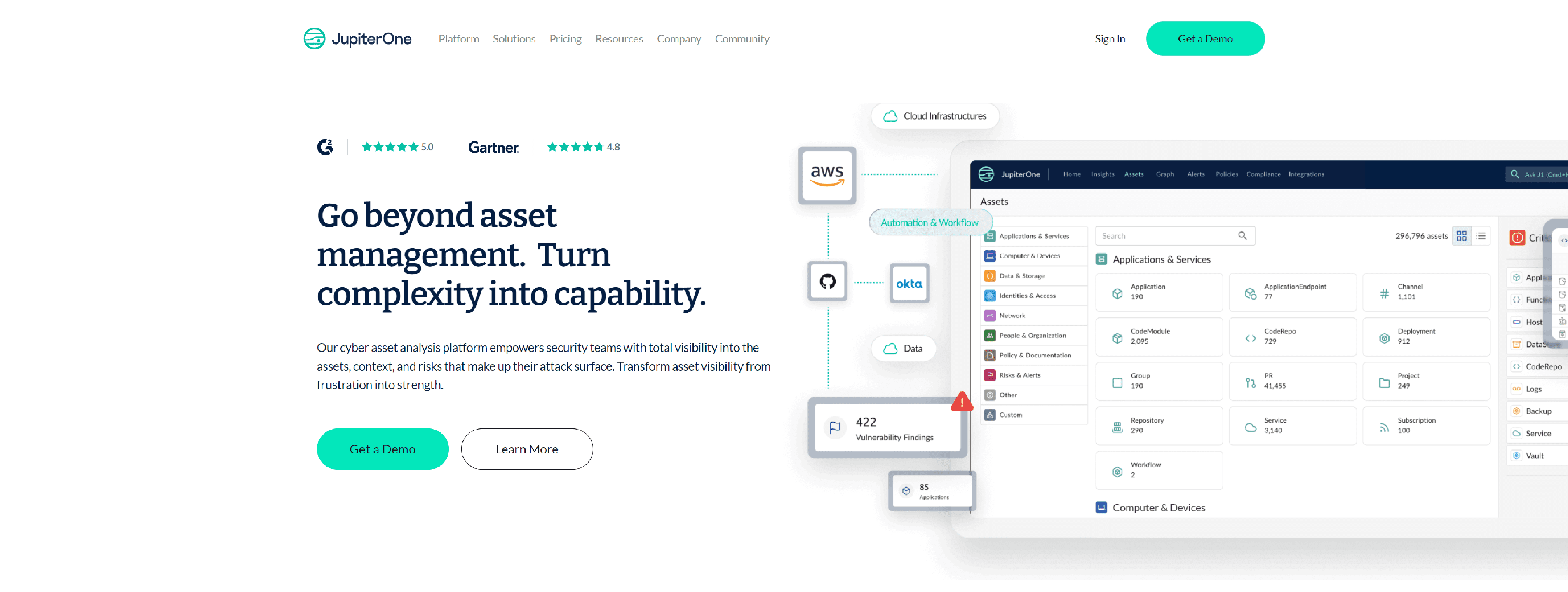
JupiterOne is a cyber asset analysis platform for cybersecurity designed to continuously collect, connect, and analyze asset data so security teams can see and secure their entire attack surface through a single platform.
- API-based, agentless setup
- Hundreds of integrations
- Scalable, graph-based architecture
- Simplified multi-cloud & hybrid environments
Top 7 several reasons why an organization may need to achieve SOC 2 compliance
- Client requirements: Many businesses, especially those in the technology sector, require their vendors and service providers to be SOC 2 compliant. This certification demonstrates that an organization has appropriate security controls in place, giving clients confidence in their ability to protect sensitive data.
- Competitive advantage: Achieving SOC 2 compliance can provide a competitive advantage in the marketplace. It shows potential customers that an organization takes information security seriously and is committed to protecting their data.
- Regulatory compliance: Certain industries are subject to specific regulatory requirements regarding the protection of customer data. SOC 2 compliance helps organizations demonstrate their adherence to these regulations, reducing the risk of fines and penalties.
- Risk management: SOC 2 compliance requires an organization to assess and manage risks effectively. By implementing the necessary security controls and monitoring procedures, organizations can mitigate the risk of data breaches and other security incidents.
- Increased customer trust: SOC 2 compliance demonstrates an organization’s commitment to data security and privacy. This, in turn, builds trust with customers, as they feel more confident that their sensitive information is being handled and stored securely.
- Internal best practices: The process of achieving SOC 2 compliance involves implementing robust security controls and practices. These measures can benefit an organization internally, enhancing overall data protection and ensuring the privacy and security of employee and company data.
- Third-party assurance: SOC 2 compliance provides assurance to stakeholders, such as investors and board members, that an organization has implemented adequate security measures to protect the data it handles. This can be particularly important for start-ups and organizations looking to secure funding or partnerships.
What are the aspects considered for selecting these SOC 2 vendors? ( Top 10 )
When selecting SOC 2 vendors, several aspects are typically considered. These aspects may vary depending on the specific needs and requirements of the organization, but some common factors include:
- Trustworthiness and reputation: The vendor’s reputation and track record for delivering secure products and services are essential. This can be assessed through reviews, customer references, and independent audits.
- SOC 2 compliance: Since the organization seeks SOC 2 compliance, it is crucial to ensure that the vendor has already achieved or is willing to undergo SOC 2 audits. Their compliance with relevant security controls, such as the Trust Services Criteria (TSC), is paramount.
- Security capabilities: The vendor should have strong security measures in place to protect data and systems. This includes physical security of their facilities, network security, encryption, access controls, and incident response plans.
- Data privacy and confidentiality: The vendor should have policies and procedures to safeguard all sensitive data entrusted to them, including privacy protections and compliance with applicable data protection regulations like GDPR.
- Service level agreements (SLAs): An SLA should be established that clearly defines the vendor’s commitment to security, availability, and performance. This ensures that their services align with the organization’s needs and expectations.
- Risk management: The vendor should have robust risk management processes and protocols in place. This involves identifying potential risks, implementing mitigation measures, and regularly assessing and monitoring risk levels.
- Business continuity and disaster recovery: The vendor’s ability to recover from a disruptive event is crucial. They should have comprehensive business continuity and disaster recovery plans to minimize potential downtime.
- Data handling and storage: The organization must evaluate how the vendor handles and stores data. It includes examining their data retention policies, data segregation practices, and jurisdictional compliance.
- Third-party assessments: External audits or assessments conducted by independent third-parties provide additional validation of a vendor’s security controls and practices. These assessments could include penetration testing, vulnerability scanning, or ongoing monitoring of security controls.
- Pricing and scalability: The vendor’s pricing structure should align with the organization’s budgetary requirements. Additionally, their services should be scalable to accommodate future growth and changing needs.
FAQ
What is SOC 2 Compliance Audit?
SOC 2 (System and Organization Controls 2) Compliance Audit is an assessment conducted by an independent third-party auditor to ensure that a service organization’s systems and processes comply with the American Institute of CPAs (AICPA) Trust Services Criteria. It focuses on the organization’s security, availability, processing integrity, confidentiality, and privacy controls.
Why is SOC 2 Compliance important?
SOC 2 Compliance demonstrates that an organization has implemented effective controls to safeguard clients’ data and protect their interests. It provides assurance to clients and business partners that the service organization follows industry best practices to mitigate risks and maintain the security, privacy, and integrity of sensitive information.
What are the Trust Services Criteria?
The Trust Services Criteria are a set of principles developed by the AICPA to assess the controls in place at a service organization. There are five criteria: security, availability, processing integrity, confidentiality, and privacy. Each criterion has specific requirements against which an organization’s controls are evaluated during a SOC 2 Compliance Audit.
Who needs to undergo a SOC 2 Compliance Audit?
Any service organization that handles and processes sensitive data on behalf of its clients can benefit from a SOC 2 Compliance Audit. This includes software-as-a-service (SaaS) providers, data centers, cloud service providers, managed service providers, and any other organization that stores or processes customer data.
How long does a SOC 2 Compliance Audit take?
The duration of a SOC 2 Compliance Audit depends on various factors, including the complexity of the organization’s systems and processes, the number of locations involved, and the scope of the audit. On average, it can take several months to complete the audit, including the preparation, assessment, and final reporting stages.
What is the difference between SOC 1 and SOC 2 audits?
SOC 1 audits (also known as SSAE 18 audits) focus on evaluating the controls related to financial reporting. They are relevant to service organizations that impact their clients’ internal controls over financial reporting. On the other hand, SOC 2 audits assess controls related to security, availability, processing integrity, confidentiality, and privacy. SOC 2 audits are generally more applicable to service organizations that handle sensitive data but do not have a direct impact on financial reporting.
What are the benefits of achieving SOC 2 Compliance?
- Enhanced trust: SOC 2 Compliance provides assurance to clients and business partners that their data is treated securely and with integrity.
- Competitive advantage: Organizations with SOC 2 Compliance are often preferred by clients who require stringent security measures.
- Improved risk management: SOC 2 Compliance helps identify and address vulnerabilities, reducing the risk of data breaches and other security incidents.
- Operational efficiency: Implementing SOC 2 controls often leads to improved processes and operational efficiencies.
- Regulatory compliance: SOC 2 Compliance may help organizations meet relevant data protection and privacy regulations.
How often should an organization undergo a SOC 2 Compliance Audit?
There isn’t a prescribed frequency for SOC 2 Compliance Audits, and it depends on various factors such as contractual requirements, industry standards, and changes to the organization’s systems or processes. However, most organizations conduct SOC 2 audits annually to ensure ongoing compliance and demonstrate their commitment to data security and privacy.