In order to get a full understanding of the issues related to security in cloud computing we’ll need to make sure we starting from a solid foundation and that we’re talking the same language about the cloud. As is often the case when it comes to new technology some people mean different things when they talk about the cloud so I think it would be a great idea for us to sync up our thoughts before we go any further. I am personally a big fan of telling stories or using metaphors. So, I’m going to try to answer the question “what is the cloud” via a home building metaphor. So let us see if we can figure this out!
Let’s pretend we’re building a new house. This house will have water heaters, one or more air conditioning systems, light fixtures, a kitchen with an oven and microwave… you know, the typical house stuff with LOTS of electrical needs. We’re going to need some way to power all of these things right? One way of making sure we will have enough power is to buy a bunch of solar panels and generators to generate our own electricity. As demand requirements change over the course of the day / months we’ll find that sometimes we have lots of extra power and sometimes we might run short. For example, as it gets warmer outside we may find that we don’t quite have enough power to run the AC with our current system. What do we do? I guess we bite the bullet and go buy another generator in order to have enough electricity available to run the air conditioner. We may find that we can’t run both the microwave and the air conditioner at the same time without buying even more power generating devices. We quickly find that the problem with trying to generate our own power is that we have to plan ahead and have enough generators on hand to handle the maximum load possible even though the maximum is rarely needed. Adding to the frustration is that we have to keep those generators on hand (they have to “sit” somewhere). Plus, they’re very important to us so we would be wise to to and test them and maintain them regularly. Doing this extra testing and maintenance costs us valuable time that we could spend golfing or something instead. All of these factors make it very difficult, not to mention financially painful, to try to maintain our entire power infrastructure under our own roof.
Read also: Top 10 Best Cybersecurity Companies for Small & Midsize Business
Wouldn’t it be nice if there was some sort of way to have access to virtually unlimited electricity that was available on demand and that you would only have to pay for what you use? Oh, that’s right, there is! We can connect to the “electric cloud” (we normally call this our ‘utility company’) and they’ll generate all the power we need while at the same time only charging us for what we use!
Basically, cloud computing involves treating computing as a utility just like electricity or water. If we need more storage for our files then we just buy “storage space” and the cloud provider magically makes more space available to us without us ever having to go buy new hard disks or do anything technically difficult. If we decide we need more computing power as our business grows and our website begins to become bogged down then we can just buy more computing power from the cloud and we see changes in minutes without us having to go buy a new server, install the software, configure it just right, etc. Maybe we find ourselves needing to hire a new employee. Normally this comes with needing to buy new software, install it on their machine, configure it, and so on. But if we are using software hosted in the cloud then there’s a really good chance that we won’t have to do anything other than add a new user to our cloud. We’ll start paying for the new user, and they will immediately be able to log in to the cloud via nothing more than their own web browser and immediately have access to the information they need without management or IT having to do anything difficult!
In that last paragraph I mentioned a couple of important sectors of cloud computing without giving them a name. So let’s break that paragraph down real quick. We’ll name and discuss the two distinct types of “services” or “utilities” mentioned. Each of these are typically handled by a different cloud computing provider (or at least a different segment) of cloud computing.
If we need more storage then we just buy “storage space” and the cloud provider magically makes more space available to us without us ever having to go buy new hard disks or do anything technically difficult. If we decide we need more computing power as our business grows and our website begins to become bogged down then we can just buy more computing power from the cloud and we see changes in minutes without us having to go buy a new server, install the software, configure it just right, etc.
This is an example of Infrastructure as a Service (IaaS). This is often a huge part of the savings in both time and money of getting into cloud computing. You can increase from 2 a CPU box to a 32 CPU box by simply paying more and not having to do anything else! This is often really powerful when your computing needs are very seasonal and you can predict when you will want more computing power. You can also add more storage space as necessary with the simple click of a button… no more having to buy extra drives and install them when you’re running low on space!
Maybe we find ourselves needing to hire a new employee. Normally this comes with needing to buy new software, install it on their machine, configure it, and so on. But if we are using software hosted in the cloud then there’s a really good chance that we won’t have to do anything other than add a new user to our cloud.
This one is a little bit IaaS, but it is also Software as a Service (SaaS). If you use cloud based software such as email from goodle and productivity tools from google or office365 then you can literally remove a TON of work from your IT staff. When a new employee is hired you just add them to your account and they immediately have access to all the software they need via the cloud provider’s portal.
Elements of Computer / Data Security
Data security, or security in computing, can be broken down into three major elements. Those elements are confidentiality, integrity, and availability. In the next few paragraphs we’ll tak a look at each these elements and see what problems cloud computing can help to mitigate. We’ll also see what new issues come along with trying to assess and maintain data and computing security in the cloud.
When most people think of computer security the first thing they think of is keeping their secrets secret. For example, if I have a file stored on my computer and I have reasonably good computer security then I can feel pretty good that nobody else knows what is in the file. It’s a secret and it’s safe because only I have access. The only thing that could go wrong from a confidentiality perspective is that a burgler might come in and take my computer. Then they could, given enough time, access my super secret file. Things get a little less certain in the cloud world though. First, you don’t know for sure that the host of the cloud computing system has top of the line security preventing unwanted access. Second, you don’t know if the provider doesn’t have rogue employees that might want to steal your file and who can walk into a server room at any time to do so. You will want to discuss these issues with any cloud service provider that you choose and your choices and cost will likely vary depending on how important it is to you that your secrets remain secrets. For confidenitiality, nothing beats a computer locked in a room with no internet access, a retinal scanner, a thermal monitor, and an alarm that sounds if anyone is in the room other than the desired user. The first Mission Impossible movie shows that even that can be beaten, but it’s still better than trusting someone else to watch it for you without proper vetting first.
The second issue, and one that people think about less often in data security is integrity of data. Integrity of data just means that the data is both complete and correct… it hasn’t been altered. Let’s say Bob is a college student and he doesn’t like the C he got in computer security class. He decided he’s going to break into the university mainframe and update his grade to an A. Well, the integrity of that data is now ruined. If the professor wants to access the data it is there, but it is not right, and the professor may not even know that it is wrong for a long time, if ever. Data stored in the cloud is probably just as susceptible to integrity issues as data stored at the local level, so integrity is probably a wash.
The third issue is availability. This one is sometimes thought about separately from security, but data availability should be part of any security providers strategy or they should be booted (no pun intended). Think about it this way, if some hacker decided to denial-of-service (DOS) your website or do crash your sftp box then you better have a security plan that can deal with it. If you don’t then you can rest assured that your foe won’t have your data, but you should also be freaking out that you won’t have access to it either! Data rarely does much good if you can’t access it so availability is a critical part of your security worries. When it comes to the cloud there are several potential issues. First, what happens when New Jersey gets hit with a massive storm and power in the whole state goes out? Are your data / servers hosted there? If so, there’s a good chance you’re going to feel the pain right along with them. Second, what happens when your data host goes out of business or gets raided by the Feds because someone else using the same service does something shady. Ask all of those legitimate users of MegaUpload how they felt when it was shutdown and the entirety of data seized by the US government who felt they had no obligation to make it available to the original uploaders. I’m not bashing the decision by government – I’m mentioning it so that you can consider that it could happen to your data too… it could get caught up in the middle of the something and cause you untold pain. Another issue is that of your own internet going out. Let’s say some doofus with a backhoe accidentally clips a cable in front of your building. If your data is offsite then that data is no longer available to you. This can happen even in non-cloud scenerios, but since it can happen in cloud based scenerios too, it’s important to consider. Do you need access to your data at a moments notice? Then you need to plan accordingly and either avoid the cloud or work on some redundant solution (ala dropbox).
Now, the good news for the cloud is that it can make a huge difference in a positive way on many of these. Need to access your data, but you’re away from your normal computer? No problem if your data is in the cloud! Of course that’s assuming everything is working correctly. Is your cloud hosting provider the top security provider in the cloud computing industry? Then you’ve probably got a pretty good shot at having highly confidential data stay that way. I wouldn’t trust it, but there’s many who based on their relatively low need for confidenitiality can live with slightly raised risk in return for not having to worry about securing things themselves.
As you can see security in cloud computing is a complex game of give and take. The cloud can mean huge savings in terms of required hardware that doesn’t have to be bought and maintained as well as a reduction of people having to hired to support the hardware and systems. On the other hand the cloud automatically introduces an entirely new layer of opportunity for crackers and Murphy (murphy’s law!) to come into play and cause a stir. As cloud computing matures so will the defenses and the attack vectors and anyone considering usage of the cloud for data storage or computing resources would do well to stay up to date!
Security In Cloud Computing
If you are here it’s because you’re interesting in security in cloud computing. Becoming knowledgeable about cloud computing and the various aspects of security involved with computing in the cloud will go a long way towards making you more knowledgeable regarding computer security in general and in helping you make good decisions when it comes to the cloud.
If you’re an employee working in the technical world then it’s important that you at least have a basic understanding of cloud security in order to perform your job responsibly. This knowledge will both increase your value to your current employer and will also enhance your job prospects in the computer industry as more data processing and data storage move towards the cloud.
There are a lot of topics to get into when it comes to securing your data and working in the cloud, and security in cloud computing will help you with feel comfortable with those topics. We’ll certainly cover some ideas in passing that you may wish to further research and we’ll try to point those out as we mention them (and provide resources for you) to give you the best possible experience we can.
According to wikipedia:
Correct security controls should be implemented according to asset, threat, and vulnerability risk assessment matrices.
While cloud security concerns can be grouped into any number of dimensions (Gartner names seven while the Cloud Security Alliance identifies fourteen areas of concern) these dimensions have been aggregated into three general areas: Security and Privacy, Compliance, and Legal or Contractual Issues.
All of these items are important to understand security in cloud computing and to be able to be confident in your own choices of provider for your cloud computing needs. Even if you decide to create your own private cloud these topics will be important for you to understand.
CIPHERCLOUD

CipherCloud is a leading CASB Vendor, with presence across the globe. Our CASB+ platform helps you govern and protect data in the cloud.
- Granular Control and Monitoring of Office 365 Users and Files
- The Power of CASB+ for Your Salesforce.com Cloud
- The Power of CASB+ for Your Amazon Web Services Cloud
- Secure Content Access and Enforce Sharing Policies in Box
- Enhance Data Governance and Compliance in Google Drive
- Meet strict privacy and data protection requirements
- The Power of CASB+ for Your Microsoft Azure Cloud
- Ensure Granular Control and Activity Monitoring of ServiceNow Corporate Users and Files
- Enhance Data Governance and Compliance in Dropbox
- The Power of CASB+ for Your Adobe Analytics Cloud
- The Power of CASB+ for Your Google Cloud Platform
- The Power of CASB+ for AnyApp
KASPERSKY
Kaspersky Hybrid Cloud Security solution provides outstanding multi-layered protection to multi-cloud environments.
For Elastic and Secure Cloud Environments:
- Accelerate visibility across cloud environments for superior edge-to-edge protection.
- Detect and respond to advanced cyberthreats by harnessing the combined power of people and machines.
- Secure any cloud workload, system, network, or data with multiple controls
One Product, Any Cloud:
- Proven security for physical and virtual servers, VDI, storage, and even data channels in your private cloud.
- Advanced security controls for workloads in public clouds, including AWS and Azure.
- Meets ongoing enterprise Service Level Objectives (SLOs) by minimizing cyber-risk.
A Seamless Security Experience:
- Integration between core technologies of your cloud and its security layer via native API
- Automated security provisioning, for secure and uncompromised cloud migration
- A seamless enterprise-level security orchestration experience for any cloud
PALOALTONETWORKS
Palo Alto Networks enables your team to prevent successful cyberattacks with an automated approach that delivers consistent security across cloud, network and mobile.
Comprehensive cloud native security:
- Deliver complete visibility, automation, detection and response across any compute, network or cloud service
- Enforce hundreds of out-of-the-box governance policies that help ensure compliance and enforce good behavior
Full lifecycle:
- Eliminate issues early and prevent alert fatigue by seamlessly integrating security early and throughout the application lifecycle, from IDE, SCM, CI/CD and registries to runtime
- Leverage continuous vulnerability management and automated risk prioritization across the entire cloud native stack and lifecycle
Across any cloud:
- Monitor, secure and maintain compliance on multi- and hybrid-cloud environments with a single integrated platform
- Leverage purpose-built solutions for public clouds, such as AWS®, Google Cloud™ and Microsoft Azure®, as well as secure your on-premises investments like OpenShift®
ARMOR
Rackspace Selects Armor to Deliver Best-in-Class Security Enterprises need a platform that consolidates threat intelligence, security analytics, alerts, and response.
- Threat Detection and Response for the Cloud of Your Choice
- Stress-Free Continuous Compliance
- Protect Your Most Sensitive Workloads and Data
PWC
PwC provides industry-focused assurance, tax and advisory services to build public trust and enhance value for its clients and their stakeholders. More than 161,000 people in 154 countries across our network share their thinking, experience and solutions to develop fresh perspectives and practical advice.
- Security management
- Security awareness and education
- Threat and vulnerability management
- Information security architecture
- Regulatory and policy compliance
- Identity and access management
- Privacy and data protection
- Physical security
- Penetration testing
- Security Operations Centres (SOC)
- Digital Identity
- Security in the cloud
BITGLASS
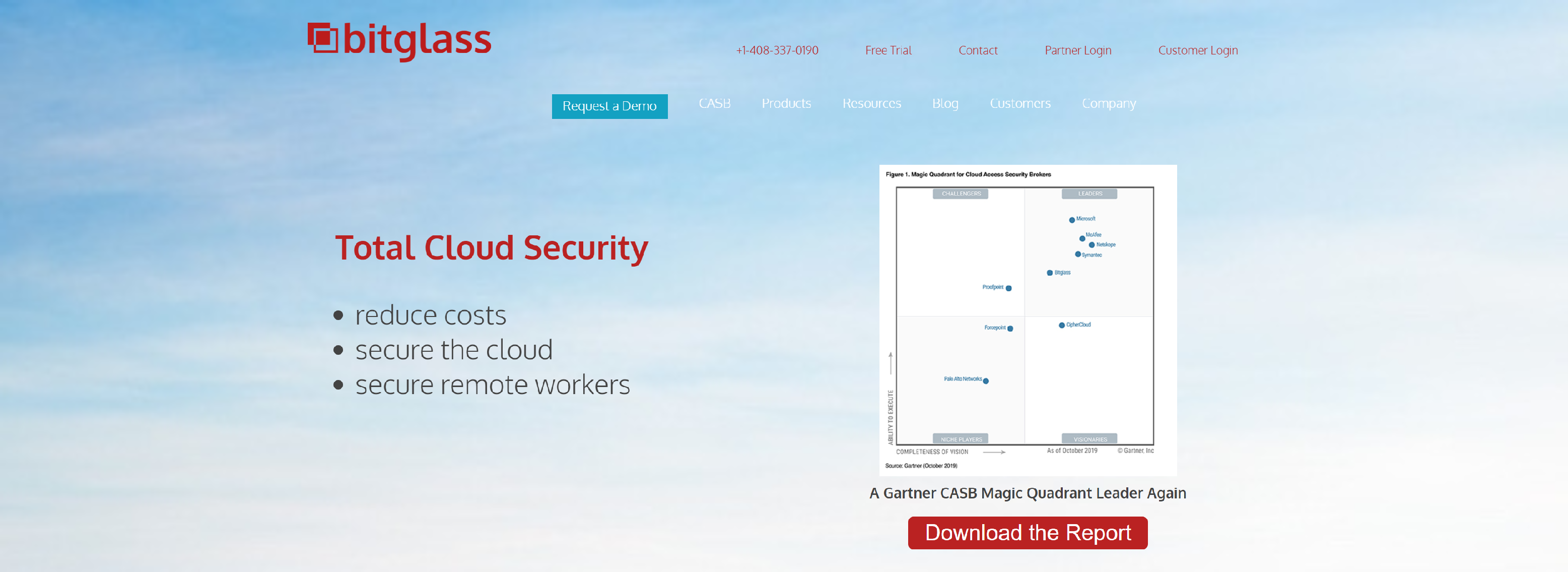
Bitglass Next-Gen CASB and SmartEdge Secure Web Gateway deliver Zero-Day data & threat protection for any app, any device, any network.
- Protect Data at Access
- Visibility and Analytics
- Real-time Security without Agents
AQUASEC
Full dev-to-prod container security solution on Kubernetes, Docker, OpenShift, Fargate, Lambda, AWS & other container platforms.
- Automate DevSecOps: security and speed without compromise
- Modern Container Security For Cloud Native Apps
- Prove Regulatory Compliance
- Protect Workloads in Serverless Containers and Functions
- Hybrid Cloud and Multi-Cloud Architecture: Security Built In
- Protect VMs Across Cloud Native Environments
THREATSTACK
Threat Stack provides full stack cloud security observability and compliance for infrastructure and applications.
- With the Threat Stack Cloud SecOps Program℠, our cloud security experts become part of your team
- With Oversight, a Threat Stack security expert continuously monitors your Threat Stack Cloud Security Platform® and alerts you to signs of intrusion and risky behavior
- With Insight, you’ll receive the continuous monitoring of Oversight, plus monthly reporting and curated analytics from your Threat Stack security engineer
DOME9
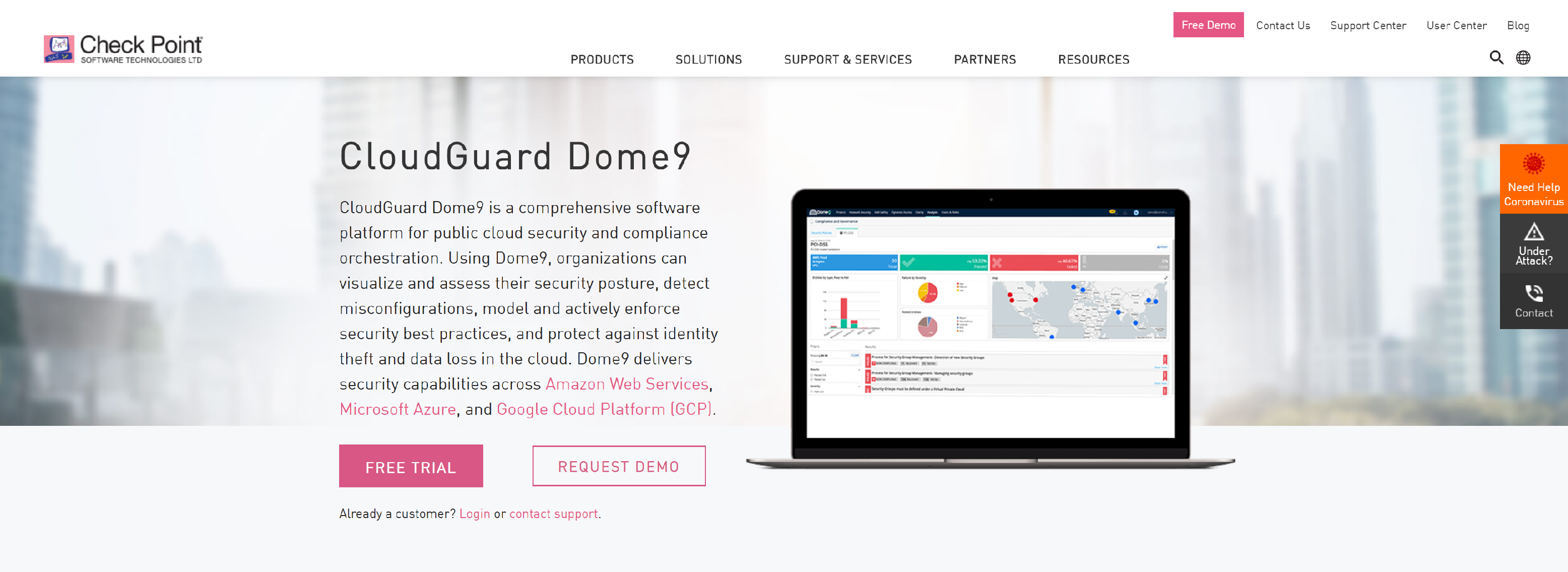
Dome9 delivers full visibility, control and faster time to protection as organizations scale in AWS, Azure and Google Cloud environments.
- Cloud Security Operations
- Compliance and Governance
- Privileged Identity Protection
- Cloud Security Analytics
CYSCALE
Cloud Security and Management Platform, Enterprise DevOps, SecDevOps, Cloud Migration, Cybersecurity AI, Cybersecurity Big Data.
- Control and Visibility
- Multi-Cloud Management
- Compliance & Regulatory
- Cloud-Native Security
- Cloud Studio Editor
IBM
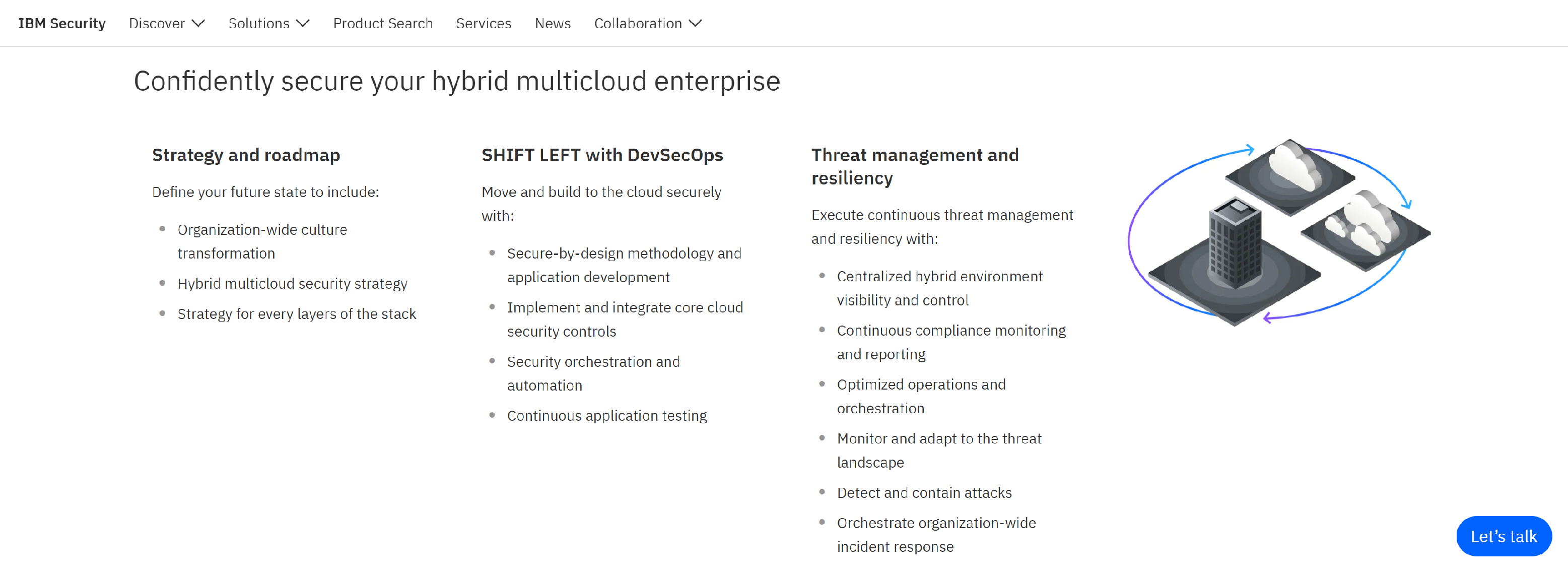
IBM Security provides security for your hybrid cloud environment by integrating security into every phase of your journey.
- Cloud security strategy
- Data protection
- Workload protection
- Identity and access management
- Threat management and compliance
ZSCALER
Zscaler is revolutionizing cloud security by empowering organizations to embrace cloud efficiency, intelligence, and agility securely.
- Secure Web Gateways
- Cloud Firewall
- Cloud IPS
- Cloud Sandbox
- Cloud DLP
- Cloud Application Control
- Bandwidth Control
- Remote Browser Isolation
- Cloud Access Security Broker (CASB)
- Cloud Security Posture Management (CSPM)
SOPHOS
Sophos is Cybersecurity Evolved. Advanced Endpoint Protection and Network Security Fully Synchronized in Real Time.
- Endpoint protection with artificial intelligence
- Firewall with synchronized security built in
- 24/7 threat hunting, detection, and response
- Public cloud visibility and threat response
- Sophos Central
- Sophos Email
- UTM
- Intercept X for Server
- Secure Web Gateway
- Sophos Wireless
- Sophos Mobile
- Phish Threat
- SafeGuard Encryption