When it comes to IT security, cloud computing presents a unique challenge. With data and applications residing on servers that are not under the direct control of the organization, it becomes essential to ensure that sensitive information is properly protected. This is where cloud workload protection platforms (CWPPs) come into play.
CWPPs are a type of security solution that helps organizations protect their cloud workloads from threats. These workloads can be anything from virtual machines to containers to serverless functions. The goal of a CWPP is to provide comprehensive protection across the entire cloud environment. This includes visibility, threat detection, and response capabilities.
The complexity of cloud environments is one of the biggest challenges when it comes to security. There are often multiple cloud providers, each with their own unique security protocols. Additionally, there may be a mix of public and private clouds, each with their own security challenges. CWPPs help to address these concerns by providing a unified security approach that crosses all cloud environments.
One of the key features of CWPPs is their ability to provide visibility into the cloud environment. This includes inventorying all cloud assets and monitoring activity across all cloud providers. This visibility is essential in identifying potential security threats, including unauthorized access attempts and abnormal behavior patterns.
Another important component of CWPPs is the ability to detect threats. These platforms use a range of security techniques to identify potential threats, including signature-based detection, behavioral analysis, and machine learning. By combining these techniques, CWPPs are able to provide comprehensive protection against both known and unknown threats.
Once a threat has been detected, CWPPs provide a range of response capabilities. This can include everything from automated response actions to alerts that prompt human intervention. The goal is to quickly and effectively address any potential security issues before they can cause harm to the organization.
In addition to these core capabilities, there are a number of other features that may be included in CWPPs. For example, some platforms may include encryption capabilities to ensure that all data is properly protected. Others may offer compliance reporting features to help organizations meet regulatory requirements.
There are a number of factors to consider when choosing a CWPP. One of the most important considerations is the compatibility of the platform with existing cloud environments. Organizations should choose a platform that is able to integrate with all cloud providers and environments they use.
Another important consideration is the scalability of the platform. As cloud environments grow and change, it’s important to choose a platform that can easily scale to meet evolving needs. Additionally, it’s important to choose a platform that provides easy-to-use management tools, so that IT teams can quickly respond to security threats without disrupting business operations.
Cloud workload protection platforms are an essential tool for ensuring the security of cloud environments. By providing comprehensive protection across all cloud providers and environments, these platforms help organizations to confidently utilize the benefits of cloud computing without sacrificing security. As organizations continue to adopt cloud technologies, the use of CWPPs will become increasingly important in maintaining a strong security posture.
PINGSAFE
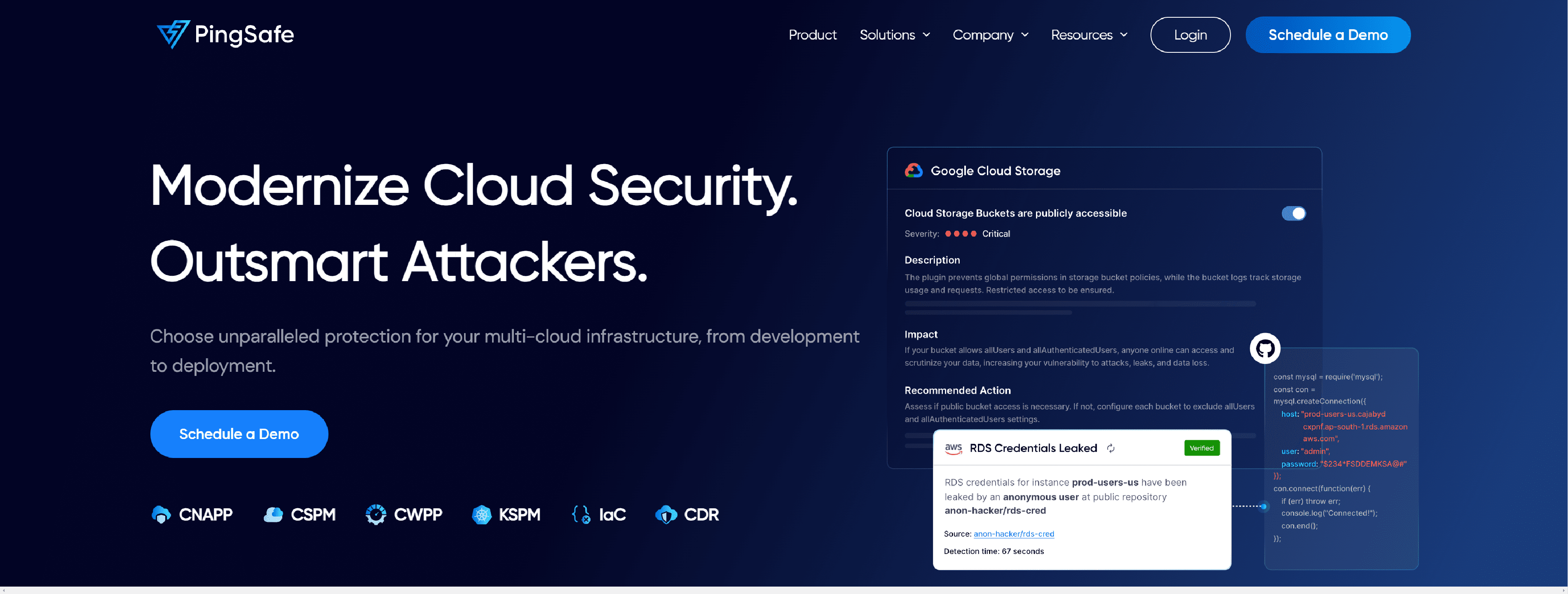
PingSafe – unified cloud security platform with CNAPP, CSMP, CWPP, CDR & CIEM solutions to secure your multi-cloud infrastructure.
- Comprehensive visibility equals better compliance
- Proof of Exploitability with PingSafe
- Eliminate the menace of Secret Leakage
- Shift Left & do right
SKYHIGHSECURITY
Skyhigh’s CNAPP solution supported by CWPP focus on Zero Trust network and workload policies.
- Improved Cloud Security Posture Management
- Centralized Data Security Policy Management
- Centralized Incident Management
ZSCALER
Zscaler for Workloads, you can reduce your costs by 30% or more and eliminate security policies by up to 90% with its innovative zero trust architecture.
- Boost efficiency with native guardrails in dev and DevOps tools
- Enforce immutability by eliminating configuration drift
- Cover 100% of workloads with agentless deployment
- Neutralize the attack surface with a zero trust architecture
- Prevent lateral movement
HILLSTONENET
Hillstone’s CloudArmour is a cloud workload protection platform (CWPP) that provides comprehensive protection for all cloud workloads, including containers, VMs and other execution environments.
- Easy integration into DevOps pipelines
- Multi-cloud and hybrid cloud support
- Wide range of workload coverage
- Host and container dual protection
- Micro-segmentation and intrusion capabilities
- Comprehensive single-dashboard visibility
UPTYCS
Uptycs, the first unified CNAPP and XDR solution, reduces risk from threats, vulnerabilities and misconfigurations all from a single UI and data model.
- Workload Security Observability for Hosts, VMs, Containers, and MicroVMs
- Security Observability for the Cloud Control Plane
- Continuous Monitoring for Best Practices and Compliance
- Cloud-Native Applications Focus
AQUASEC
Aqua – secure cloud-based workloads with one platform that works across hybrid and multi-cloud environments to stopkKnown & Zero-Day Attacks.
- Runtime security
- Enforcement for Every Workload
- Vulnerability and Risk Scanning
- Advanced Malware Protection
- Designed for Cloud
- Centralized Workload Management
TENCENTCLOUD
Based on Tencent Security massive amounts of threat data, Cloud Workload Protection Platform (CWPP) leverages machine learning to provide a wide variety of security protection services, including asset management, trojan detection and prevention, intrusion detection, vulnerability alerting, and security baseline.
- Asset Management
- Virus Scan
- Intrusion Defense
- Vulnerability Scan
- Security Baseline
- Core File Monitoring
BITDEFENDER
Bitdefender GravityZone is designed for virtualized and hybrid cloud environments. The enterprise-grade cloud workload protection platform that you need.
- Advanced Defenses
- Single Console
- Clean Architecture
- Universal Compatibility
- Cost Efficient
- Optimized Scanning
SYNOPSYS
![]()
Synopsys has partnered with industry-leading cloud providers – Microsoft Azure, Amazon Web Services, and Google Cloud – to optimize infrastructure configurations, removing the guesswork so EDA can be rapidly deployed on the cloud.
- RTL & Gate-Level Simulations
- Static Timing Analysis (STA)
- Comprehensive Physical Verification
- Robust Cloud Optimized Flows
ORCA.SECURITY

Orca offers industry-leading agentless Cloud Workload Protection Platform (CWPP) capabilities and provides 100% coverage and visibility into cloud workloads.
- Cloud native vulnerability management
- Protect your sensitive data
- Detect known and unknown malware
SOPHOS
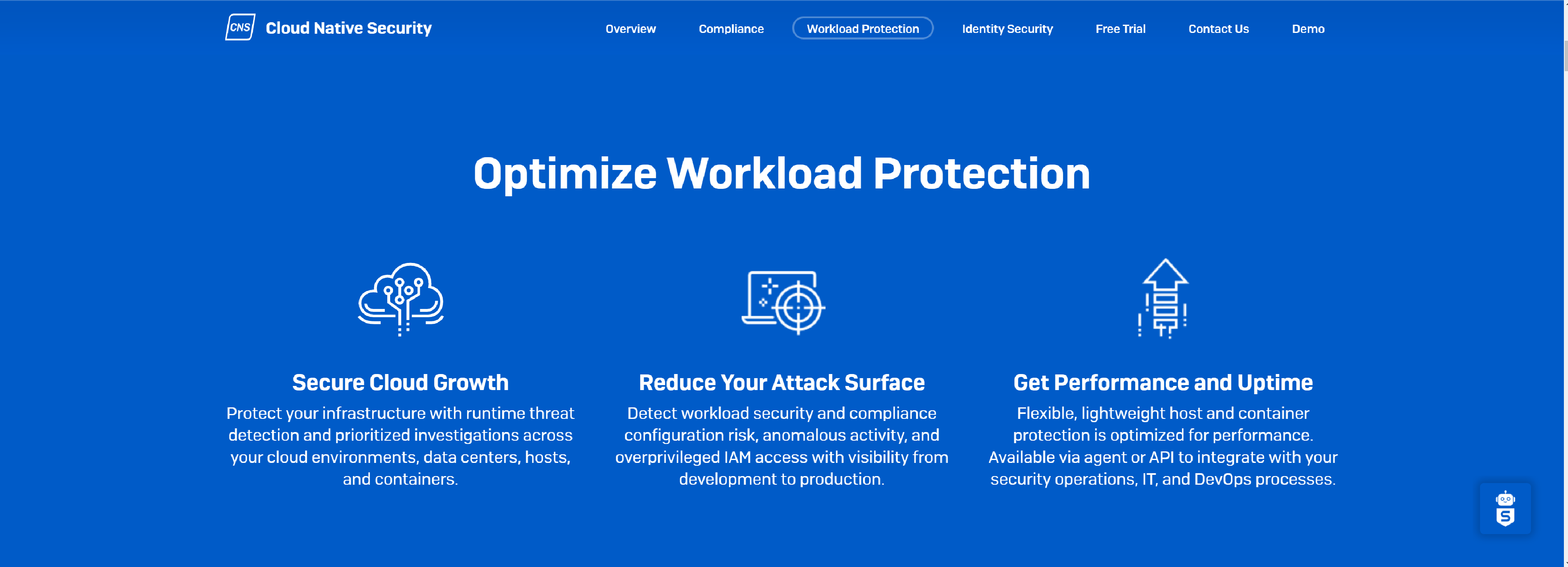
Sophos Workload Protection provides complete visibility into your host and container workloads, identifying malware, exploits, and anomalous behavior before they get a foothold.
- Integrate with Security, IT, and DevOps
- Get Performance Without Friction
- Automate Your Cloud Security Checklist
- Get Flexible Host and Container Protection
- Resolve Security Incidents Faster
- Hunt for Threats and Strengthen Your IT Operations
- Take the Weight of Cloud Security Off Your Shoulders
- Respond to Security Incidents at 3 a.m.
JUNIPER
Juniper Cloud Workload Protection defends application workloads in any cloud or on-premises environment and against advanced and zero-day exploits automatically as they happen.
- Run-time Protection
- Sophisticated Attack Prevention
- Vulnerability Detection
- Comprehensive Telemetry
- Minimal False Alerts
- Zero Trust Microsegmentation
ILLUMIO

Illumio – trust the leader in Zero Trust Segmentation to protect against ransomware and isolate cyberattacks from spreading across any cloud, data center, or endpoint.
- Cloud blind spots
- Application awareness
- Security gaps
CISCO
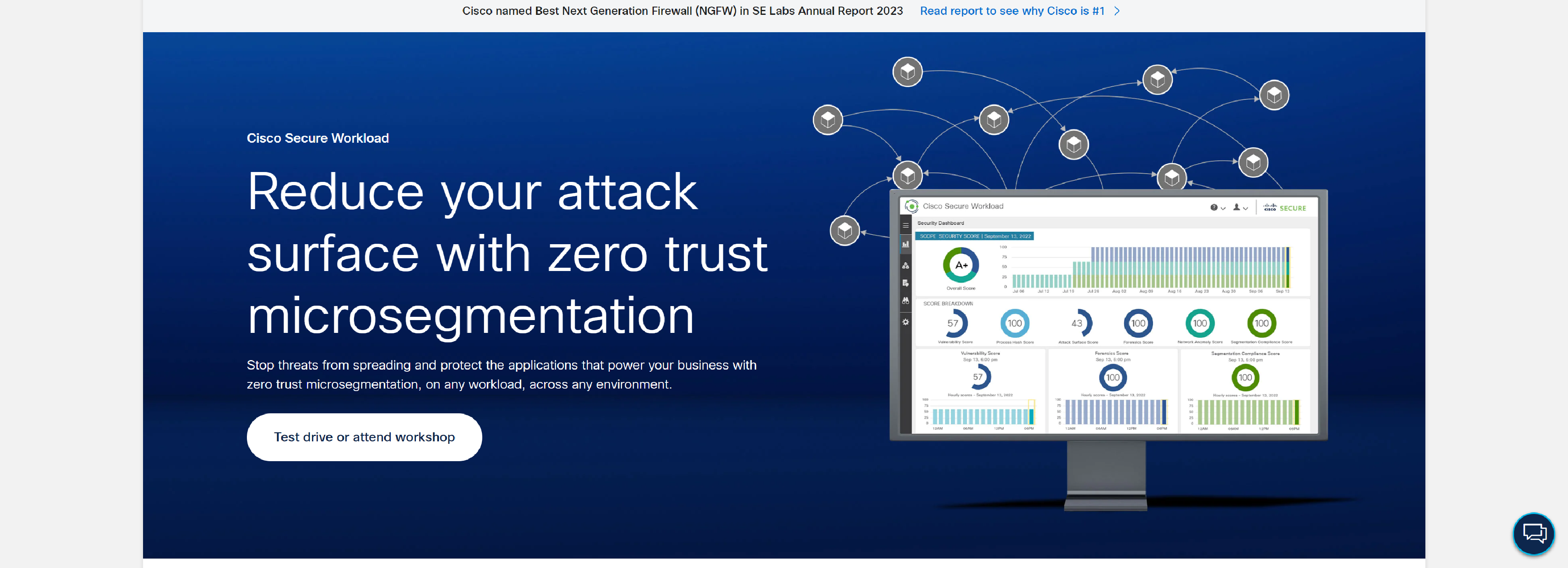
Cisco Secure Workload stops lateral threats and reduces your attack surface with zero-trust microsegmentation. Automate policies and simplify cloud migration.