PCI DSS. What does this mean? Does PCI DSS affect me? Well, if you sell a product or service and accept credit cards as a payment option then the answer is yes. Compliance is mandatory and failure to achieve compliance can result in fines, forensic investigation fees, inability to process credit cards and ultimately loss of trust from your customers and a damaged reputation!
Ouch! Okay, enough of the scary stuff, let’s start with a little background and define the applicable terms before we get into what all of this really means to you; the business owner, compliance officer, security manger or the like.
PCI DSS, or the Payment Card Industry Data Security Standard is the payment card industry’s (or credit card companies) generally accepted set of standards to protect cardholder information. Cardholder information is the data used to process credit card payments via the Internet, point of sale (POS) terminals or card-in-hand via the telephone or a swipe of the magnetic stripe.
The Payment Card Industry has become more and more formalized over recent years as a response to the increasing instances of security breaches resulting in compromised cardholder information. In a nutshell the major card companies got together and said enough is enough. They were tired of floating the cost of stolen card data and the subsequent purchases that the cardholder was not and is not responsible for. The real issue really bubbled to the surface with the exponential growth of electronic commerce or ecommerce. Ecommerce is currently growing four times faster then offline sales and has already totaled more than $33 billion during the first quarter of 2019. The huge growth in online sales means more credit card information flying around the electronic highways. The even bigger problem is the storage of the credit card / cardholder data. Ecommerce is driven by online stores and online stores capture credit card information and store it is databases. The ecommerce database is a great centralized repository of cardholder data that, when compromised, results in huge liabilities for the credit card issuers and acquiring banks. The result of all of this frustration was the formation of the Payment Card Industry and the PCI Security Standards Council. Yes, there is now a governing council.
The PCI Security Standards Council is a Limited Liability Corporation (LLC) chartered in Delaware, USA. The PCI Security Standards Council was founded by American Express, Discover Financial Services, JCB International, MasterCard Worldwide, and Visa Inc. All five payment brands share equally in the council’s governance, have equal input to the PCI Security Standards Council and share responsibility for carrying out the work of the organization. All of the five founding members have agreed to incorporate the PCI DSS as the technical requirements of each of their data security compliance programs.
Now that we’re all caught up on the history / background of the PCI DSS and the governing council we can really get to the nuts and bolts of what all of this really means to you. I have been asked many times by compliance officers, general counsels and the moms and pops of the mom and pop shops as to what they should be doing right now to be compliant and ultimately reduce the risk of being able to accept credit cards and or pay fines levied upon their business(s). That’s what it all really comes down to now, isn’t it? Owners, officers and managers want to run their business and organizations to the fullest potential while minimizing risk to themselves, their businesses and organizations and their coveted customers that pay the bills and allow the lights to stay on…albeit virtually.
The first step for most of us is to define our level as a merchant. Defining our merchant level allows us to review and ultimately obtain our appropriate level of compliance.
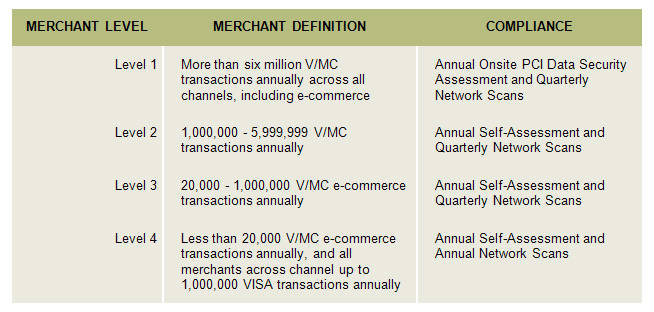
As you can see, the levels above include all merchants that process / accept credit cards. The requirements for compliance now apply to everyone! The only changes to the tiered requirements are on the newly released scaled Self Assessment Questionnaire. It should also be noted that the merchant definitions listed above are total annual transactions.
Once your compliance level has level has been defined it is time to complete the applicable requirements and submit your attestation of compliance. All merchant levels require completion of an annual security assessment. Levels 2, 3 and 4 require a self assessment while level 1 merchants must have a qualified security assessor review their compliance and submit an opinion on report accuracy.
The assessment is based on the 12 over-arching control objectives of the Payment Card Industry Data Security Standards. The current version of the standard specifies 12 requirements for compliance, organized into 6 logically related groups, which are called “control objectives.”
The control objectives and their requirements are:

The control objectives listed above dictate the requirements for compliance. The assessment is based on the control objectives and the associated data security standards. All in all there are over 200 data security standards that drive the control objectives. Achieving your compliance initially is no easy task indeed, but it is doable when broken down and looked at requirement by requirement. The first time is always the hardest and a lot of the work is producing the appropriate documentation to support your work. Supporting documentation is not required, but is really encouraged to allow for continued ease of maintenance of your compliance program as well as the ability to produce evidence of compliance with the DSS in the event of a breach and possible audit. Once the control objectives are complete, documented and fully squared away, it is time to call a qualified scan vendor and have a vulnerability assessment of your PCI in-scope environment.
You must contact one of the qualified assessors to have them perform an external vulnerability assessment of your PCI in-scope environment. The vulnerability assessments must be performed quarterly. A failing scan results in non-compliance status, so all failures must be remediated timely. The vulnerability assessment, or scan, is performed from outside your organization and only focuses on the servers and network devices that house, process and transmit customer cardholder information (credit card data). The scan looks for common vulnerabilities and holes in the patch levels and protocols. You will have to ensure all of the in-scope devices are adequately patched, ports not utilized are closed and risky protocols / software versions are updated or removed. Please look for a future article coming out soon detailing how to identify and secure your environment and ultimately prepare for a network vulnerability assessment.
So that is it! It doesn’t seem too bad does it? There are the two overall major requirements consisting of the scan and the questionnaire. As mentioned the questionnaire is catered to your merchant level. Please note that most of the article focuses on level 2, 3, and 4 merchants as I feel level 1 merchants usually do, and should, hire outside help.