Kubernetes security posture management (KSPM) is a term that refers to the process of managing and maintaining the security of a Kubernetes cluster infrastructure. As Kubernetes has become the de facto standard for container orchestration, ensuring the security of the cluster is of paramount importance to protect sensitive data, prevent unauthorized access, and prevent potential security breaches.
In a Kubernetes environment, the security posture refers to the overall security stance of the cluster, including all its components, configurations, and policies. Managing this security posture involves implementing a combination of best practices, security controls, and continuous monitoring to ensure that the cluster remains secure and compliant with security standards.
One key aspect of Kubernetes security posture management is securing the cluster’s network. Kubernetes operates in a distributed and dynamic network environment, making it crucial to secure communication channels between its components. This can be achieved through network policies, which define rules for inbound and outbound traffic to and from the cluster. Additionally, network segmentation can be implemented to isolate sensitive workloads and prevent lateral movement in case of a breach.
Another important aspect of security posture management is managing access controls. Kubernetes uses RBAC (Role-Based Access Control) to manage user permissions and limit what actions each user can perform within the cluster. It is important to carefully define roles and permissions, ensuring that only authorized users have access to critical operations or sensitive resources. Implementing multi-factor authentication (MFA) and regularly rotating credentials is also recommended to prevent unauthorized access.
Securing container images is another essential part of managing the security posture. Container images can be a potential entry point for attackers, as they may contain vulnerabilities or malicious code. Regularly scanning and updating container images for security vulnerabilities, using image signing and verifying mechanisms, and implementing container image policies can help maintain a secure image supply chain.
Continuous monitoring and logging are integral to security posture management. Kubernetes provides various logging and monitoring mechanisms that allow administrators to track and analyze activities within the cluster. Monitoring tools can help identify unusual activity, detect and alert on potential security incidents, and provide insights for further security improvements.
Regular assessment and auditing of the cluster’s security posture is also important. Conducting periodic security audits helps identify potential vulnerabilities, misconfigurations, or weaknesses in the cluster’s security controls. This could involve manual code reviews, penetration testing, or the use of automated security scanning tools. Remediation actions should be taken promptly to address any identified security gaps.
Compliance with security standards and regulations is another critical aspect of Kubernetes security posture management. Depending on the industry and geographic region, organizations may need to comply with various security standards, such as PCI DSS, HIPAA, or GDPR. Ensuring that the Kubernetes cluster adheres to these standards requires careful implementation of security controls and regular validation of compliance.
Kubernetes security posture management is a comprehensive process that involves managing and maintaining the overall security stance of a Kubernetes cluster infrastructure. It encompasses network security, access controls, container image security, monitoring, auditing, and compliance. By following best practices and implementing appropriate security controls, organizations can ensure the security and integrity of their Kubernetes environments.
Discover the top 10 best Kubernetes Security Posture Management (KSPM) Solution Providers
PINGSAFE
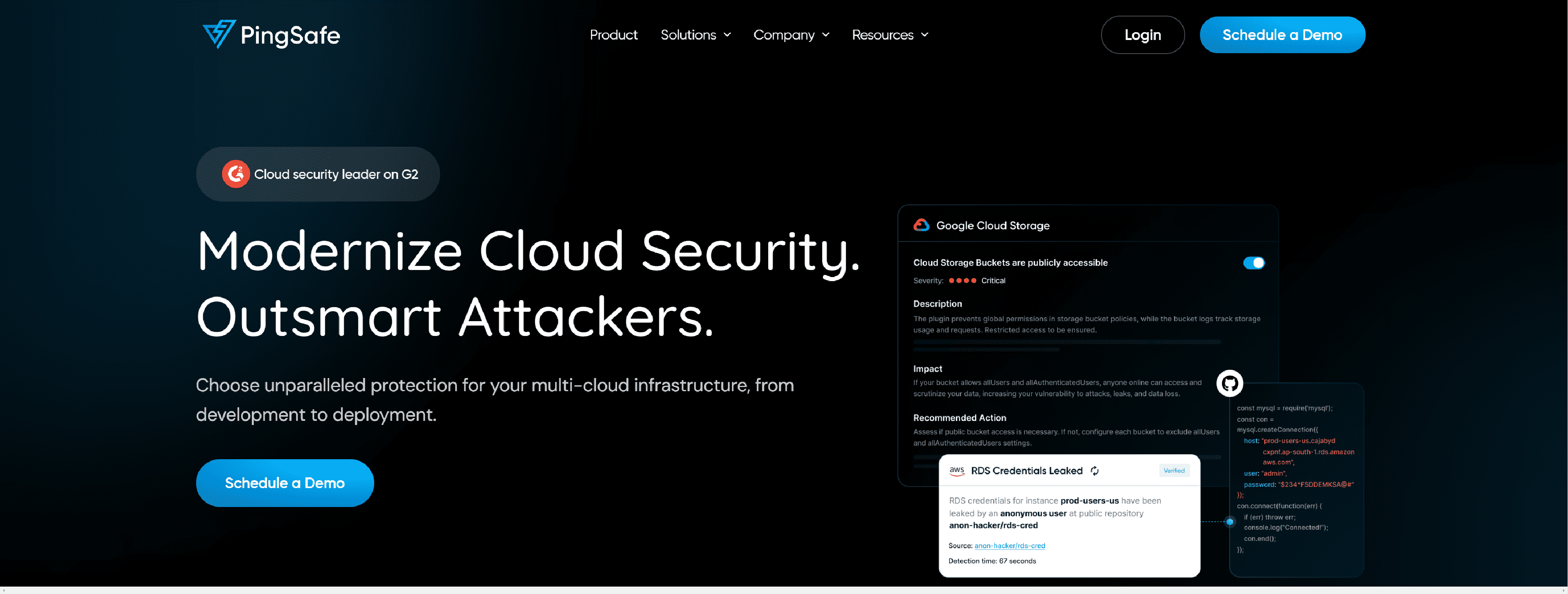
PingSafe is a Cloud-native Application Protection Platform (CNAPP) that combines the powers of CSPM, CWPP, KSPM, IaC scanning, and real-time cloud detection and response.
Key Features:
- Zero False-Positives
- Easy & Agentless Onboarding
- 100% Visibility with Real-Time Monitoring
- Intelligent Compliance Monitoring
- Offensive Security Engine
WIZ.IO

Wiz – holistically secure containers, Kubernetes, and cloud environments from build-time to real-time.
- Graph-based risk correlation and prioritization
- Real-time threat detection
- Automatic Kubernetes Security Posture Management (KSPM)
- Enable guardrails across the development pipeline
ERMETIC
Ermetic reveals and prioritizes security gaps in AWS, Azure and GCP and enables organizations to remediate them immediately.
- Unified Visibility and Asset Management
- Full-Stack Risk Assestment for Kubernetes Security
- Remediation for Accelerated Risk Reduction
- Anomaly Detection and Threat Investigation
- Compliance Audit and Automated Reporting
- Full Cloud-Native Security across the Lifecycle
CHECKPOINT
Check Point Infinity architecture delivers consolidated Gen V cyber security across networks, cloud, and mobile environments.
- Image Security Scanning
- Credential Exposure
- Integrated Container Security
SYSDIG
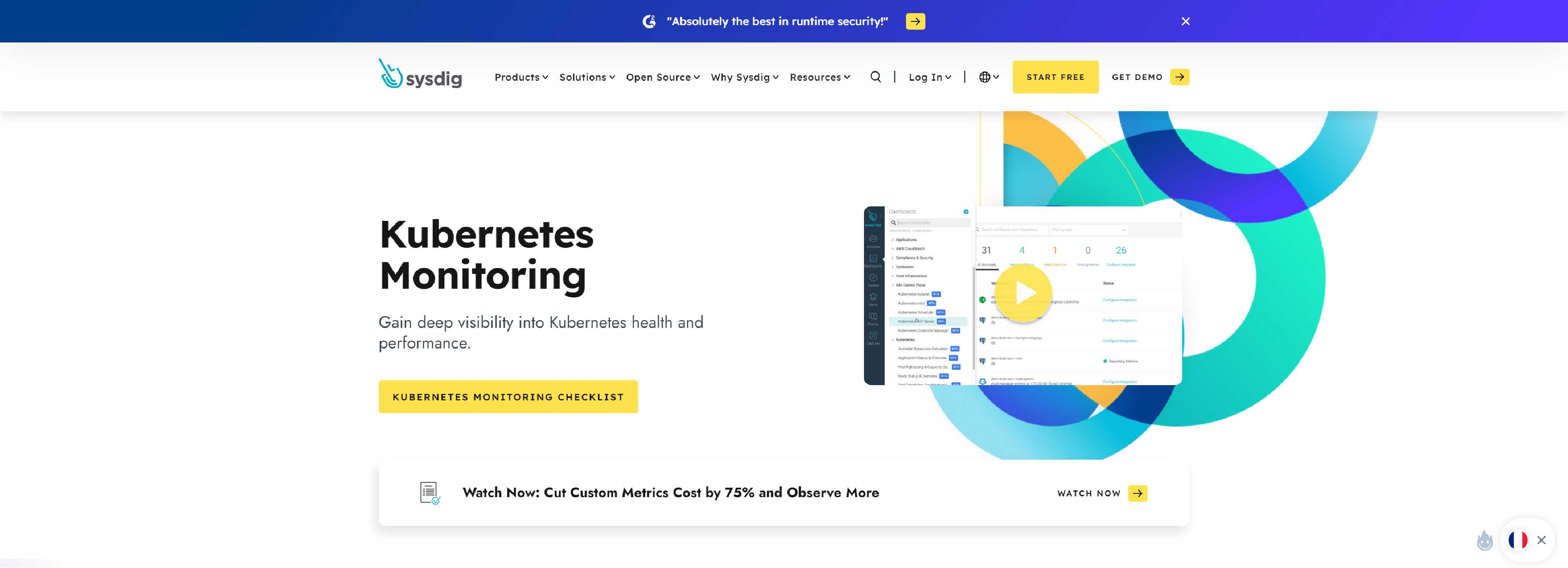
Kubernetes monitoring with Sysdig Monitor lets you inspect every aspect of your Kubernetes Clusters with full visibility to avoid potential problems.
- Troubleshooting Kubernetes Errors
- Cluster Availability and Capacity
- Cluster and Workload Status
- Resources Usage vs. Requests and Limits
RUNECAST

Runecast provides visibility of all assets across your entire estate – AWS, Azure, GCP, Kubernetes, VMware, Windows or Linux – for on-prem, hybrid or multi cloud environments.
- Compliance Management
- Remediation
- Easy Reporting
ORCA.SECURITY
Orca Security provides agentless, workload-deep, context-aware cloud infrastructure security and compliance through our comprehensive cloud security platform.
- Easy onboarding
- View every cloud asset
- Prioritize what matters
- Start fixing issues
- Always-on security
Prisma Cloud (PALOALTONETWORKS)
Prisma Cloud – a Kubernetes Certified Service Provider (KCSP) – offers cloud native security and compliance coverage throughout the entire development lifecycle.
- Cloud Security Posture Management
- Cloud Workload Protection
- cloud network security
- cloud infrastructure entitlement management
REDHAT
Red Hat is the world’s leading provider of enterprise open source solutions, including high-performing Linux, cloud, container, and Kubernetes technologies.
- Secure the software supply chain
- Protect the Kubernetes infrastructure
- Defend the workloads
SNYK
Snyk Container enables developers to easily find and automatically fix known vulnerabilities in Docker container base images, Dockerfile commands, Kubernetes workloads, and more.
- Integrated IDE checks
- Native Git scanning and monitoring
- Secure from pipeline to production
- Prioritize top container risks
PANOPTICA
Panoptica’s Kubernetes security helps to minimize the Kubernetes attack surfaces, prevent administrator errors, and protect against common attack vectors.
- Complete Kubernetes Security for Cloud-Native Applications
- Automate security configuration for multi-cloud Kubernetes
- Dynamic visual view of Kubernetes workloads
- Panoptica ensures least-privilege access
- Enhance security posture and prevent the deployment of unsafe and non-compliant workloads