Protecting the network, system, or applications from the cyber-attack is imperative for the security and privacy of your business. As more and more things move online, the risk of cyber threats in the virtual world from ransomware, malware, hackers, social engineering, and phishing continues to grow at a quick pace. IT services providers must ensure that every single computer on your network must be comprehensively protected to prevent hackers and cybercriminals from capitalizing on the vulnerability to steal sensitive data, and indulge in cyber-attacks, and identity thefts. A research report by a well-known agency reveals the rising trend of online attacks with over 30% rise in the ransomware, 32% rise in hacking attempts and 40% rise in malware attacks. Close to 90% of companies surveyed that they have been a victim of email-based spoofing, and 70% of the organizations reported an increase in impersonation fraud.
An important thing to take note of is that the use of public Wi-Fi makes your device or data more susceptible to cyber threats. According to the research performed by Norton, over 60% of the people are aware of the fact that public Wi-Fi is not safe even if it is passwords protected.
Experts suggest that a very important thing to keep in mind while choosing a security tool is its Cyber Resilience, which means the tool should possess the ability to stop cyber-attacks, and simultaneously minimize the impact of a successful attack, so that the IT infrastructure quickly gets back to its feet, and business disruption is minimized.
In the following paragraphs we shall look at top 5 tools for cyber security, and see why it is important to hire cyber security services of a top firm to minimize the risk of external attacks and breaches in the virtual world.
SolarWinds Security Event Manager
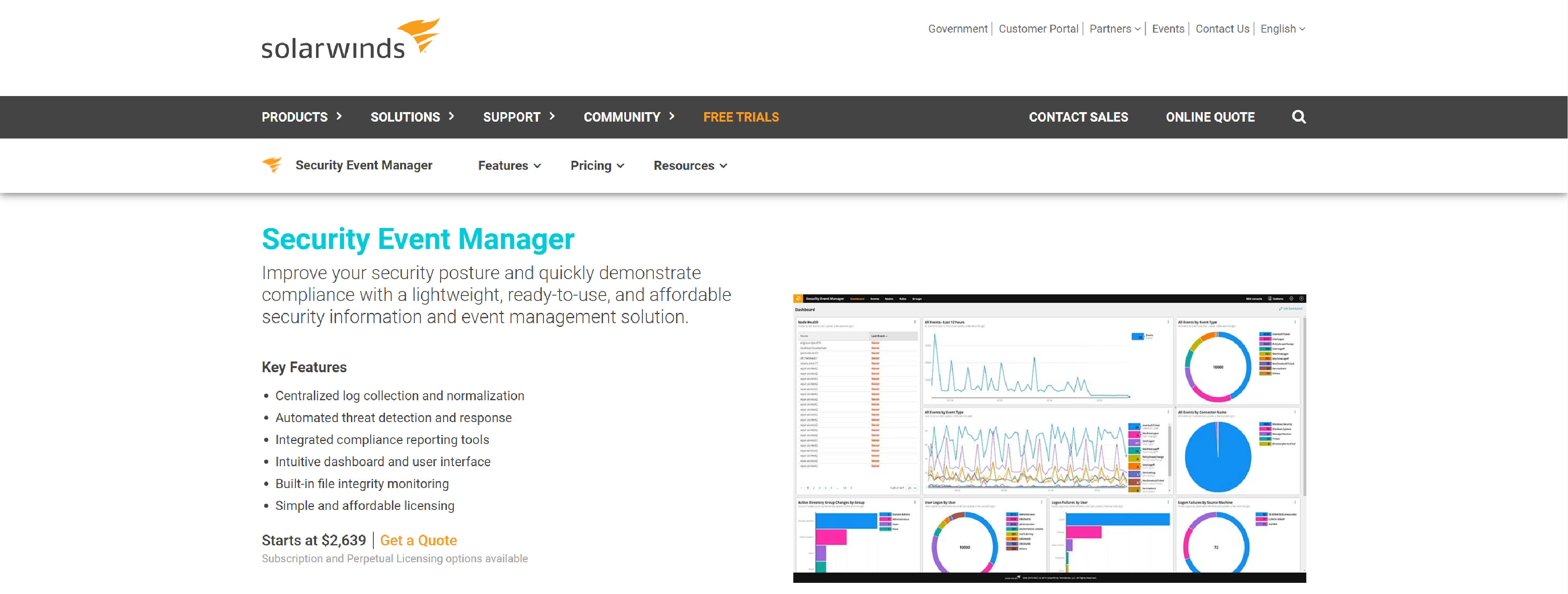
This tool is a network and host intrusion detection system ideal for both small and large businesses. It comes with a free trial offer for 14 days, and thereafter you can purchase it for $4500. SolarWinds Security Event Manager is a cloud-based scalable solution capable of perform a host of activities, including real-time monitoring, network traffic security and analysis, database management, systems management, reporting of security threats, and IT security and IT service management to name a few.
SolarWinds Features
- Automated threat detection and response
- A comprehensive set of integrated reporting tool
- Centralized log collection
- Easy-to-use dashboard
- Security Information and Event Manager
- Built-in file integrity monitoring
- Compliance reporting
- Forensic analysis
- Cyberthreat intelligence that is continuously updated
Bitdefender Total Security
Offering strong protection without impacting performance in a major way, Bitdefender Total Security is an anti-malware software, which offers good protection against cyber threats across all major operating systems, including Windows, Mac, Android, and iOS devices. You can have it for 1 year for 5 devices for $24.99 without slowing them down.
Bitdefender Features
- Real-time protection against critical data theft
- Multi-layer ransomware protection along with ransomware remediation
- Network threat intelligence and protection
- Equipped with Web Attack Prevention, Anti-Fraud, and Rescue Mode
- Complete real-time data protection and advanced threat defense
- Multi-layer ransomware protection
- Advanced parental control
Wireshark
The world’s most popular network protocol analyzer, Wireshark is best suited for commercial and non-profit enterprises, government agencies, and educational institutions. The most important feature of Wireshark is that it offers a microscopic view of your network activity, allowing you to inspect hundreds of protocols. Wireshark network protocols analyzer supports Windows, Mac, Linux, FreeBSD, Solaris, and NetBSD among others.
Wireshark Features
- Live capture and offline analysis
- Supports various protocols for decryption
- Deep inspection of hundreds of platforms
- Powerful display filters
- Rich VoIP analysis
- Export output to XML, PostScript, CSV, or plain text
Mimecast
Mimecast is a cloud-based platform ideal for all small and large enterprises. It scores high grades on email security and cyber resilience. It provides multiple products and services such as email security, threat protection, web security, cloud archiving and Web security among others. It is best known for its email security feature, which offers protection from attacks like ransomware, impersonation, etc. Inappropriate websites containing malware and malicious content can easily be blocked with the help of Mimecast.
Mimecast features
- Email Security with threat protection offered from impersonation, spear-phishing, ransomware, and few other types of targeted attacks.
- It offers automated content control and data loss prevention.
- It provides web security by blocking inappropriate business websites and protecting against user-initiated malicious web activity & malware.
- It provides a Cloud Archiving facility for archiving files, emailing, and other valuable data.
Norton LifeLock
A large number of organizations these days store personal data of employees. As such, the possibility of large-scale data breach and identity-theft is always present. Norton offers comprehensive protection against such threats with Norton 360 with LifeLock. It comes with features such as intrusion prevention wall, powerful erase and repair, antivirus file scan, malware protection, cloud backup, and secure VPN.
Norton LifeLock features
- Identity and social security number alerts
- Norton Password Manager is a simple, secure, and smart solution for managing passwords.
- Phone takeover monitoring
- Secure Norton VPN
- Alerts on crimes committed in your name
- Credit reports and scores
- Cloud backup services to store and protect files and documents.
- Home title monitoring
- Social media monitoring
Conclusion
Organizations work with mammoth amount of data these days. It is important to protect this data so that the business can operate smoothly. This can be achieved through sophisticated cyber security tools that can protect a business from malware and data breaches through several security measures.