Cybersecurity for businesses is all about protecting an organization’s computer-based equipments and information from unintended or unauthorised access, theft, change or exploitation. Whether an organization thinks of implementing cloud computing or simply maintaining a website and using emails, cyber security for businesses ought to be an integral part of the plan.
Importance of Cybersecurity for Businesses
Theft of digital information is among the most often reported fraudulence, surpassing physical theft. Every business which uses the Internet is liable for building a culture of security which will greatly enhance business and consumer confidence. Good cyber security for businesses can boost the reputation of the company and open up new business opportunities.
Read also: Top 13 Cloud Security Companies And Service Vendors To Watch
Understanding Types of Cyber attacks
Regardless of the motive, numerous cyber attackers use one of many prevalent strategies and therefore it’s very vital to have a competent cyber security for businesses.
APT – Advanced persistent threats are targeted long-term cyber attacks which break into a system network in several phases in order to avoid detection.
DDoS – Distributed Denial of Service, happen when a server is deliberately inundated with requests, with all the intention of shutting down the target’s network system or website.
Inside attack – An individual with administrative privileges or particular person pretending to be a representative generally from within the company, maliciously misuses his/her credentials to get access to confidential information data of the company.
Malware – includes any program for example viruses or spyware that is introduced in to the target’s computer system with the intention to cause harm or acquire unauthorised access.
Password attacks – Cracking a password is the easiest method for cyber criminals to gain entry to their target’s company accounts and databases.
Phishing – entails collecting delicate information like sign in credentials and credit card info via a legitimate looking but eventually fraudulent website, usually sent to naive individuals in an email.
Ways to enhance cybersecurity for businesses
Scope out the cyber threats
If cyber security for businesses is to be a success, leaders have to determine where the cyber threats for businesses begin and what’s being targeted.
Choose a Leader
Selecting the best person to steer the cyber security for businesses and its plan is essential .No matter whether it’s COO or CFO, the precise responsibilities will be different substantially depending on company and the way threat levels are understood. What’s obvious is that they have to be consistently conversing with the executive committee and be contemplating across the company, instead of being his or her own silo. Crucial decisions associated with the cyber security for businesses can’t be left only at the disposal of the IT function.
Build a strong cyber defense system
Back in the corporate and business world, cyber security for businesses continues to be deemed as a purely technical issue. The businesses need to comprehend that it’s the lynchpin for protecting their most valuable assets including the intellectual property, financial data, customer information, employee records, and even more. The threat of cyber hackers and cyber criminals is extremely real, for big companies and smaller businesses as well. This means that business owners must take on that a strong cyber-defense system is absolutely essential in the contemporary business world to be able to take care of the cyber security for businesses.
Invest in security consulting services
To prevent any computer network security problems that influences the customers of the business, it is quite important to spend money on security consulting services to recognize vulnerable areas within the existing cyber security setup and they might help fulfill all of the requirements needed to enhance the cyber security for businesses to make sure that the customers should never be adversely troubled by a security or data violation and thus the cyber security of businesses can become more powerful and more secure.
Collaboration and cooperation
To tackle cybercrime proficiently, it is important to build dynamic partnerships and cooperation involving the private sectors, financial institutions, information security organizations and public institutions to analyze cybercrime, to monitor financial market transactions and to impose laws. Without productive private and public cooperation, cybercrime should never be tackled successfully and we can’t ever be able to bring in cyber security for businesses.
Continuous reassessment of the company’s Position
Investment in cybersecurity for businesses should no longer be seen as one-off, technological fix. Management need to routinely devote money and time into evaluating the threats, their methods and cultural procedures, or they’ll easily discover themselves at an increased risk.
In today’s global and digital world, data rule. Protecting intellectual property, company’s reputation and financial information is a vital part of the business strategy. However with the amount of threats and the complexity of attacks escalating, it is a formidable challenge.
SCIENCESOFT

In cybersecurity since 2005, ScienceSoft helps enterprises ensure the highest level IT infrastructure protection.
- Cybersecurity consulting
- Security testing of IT infrastructure and its components (infrastructure security audit, penetration testing, vulnerability assessment,)
- Application security (security code review, web / mobile / cloud / IoT security)
- APT protection
- Identity and access management
- Network protection (SIEM, DDoS and DoS protection, email security; firewalls, IDS/IPS, DLP implementation and setting; antivirus protection)
- Managed Security Services
SYNEIDIS
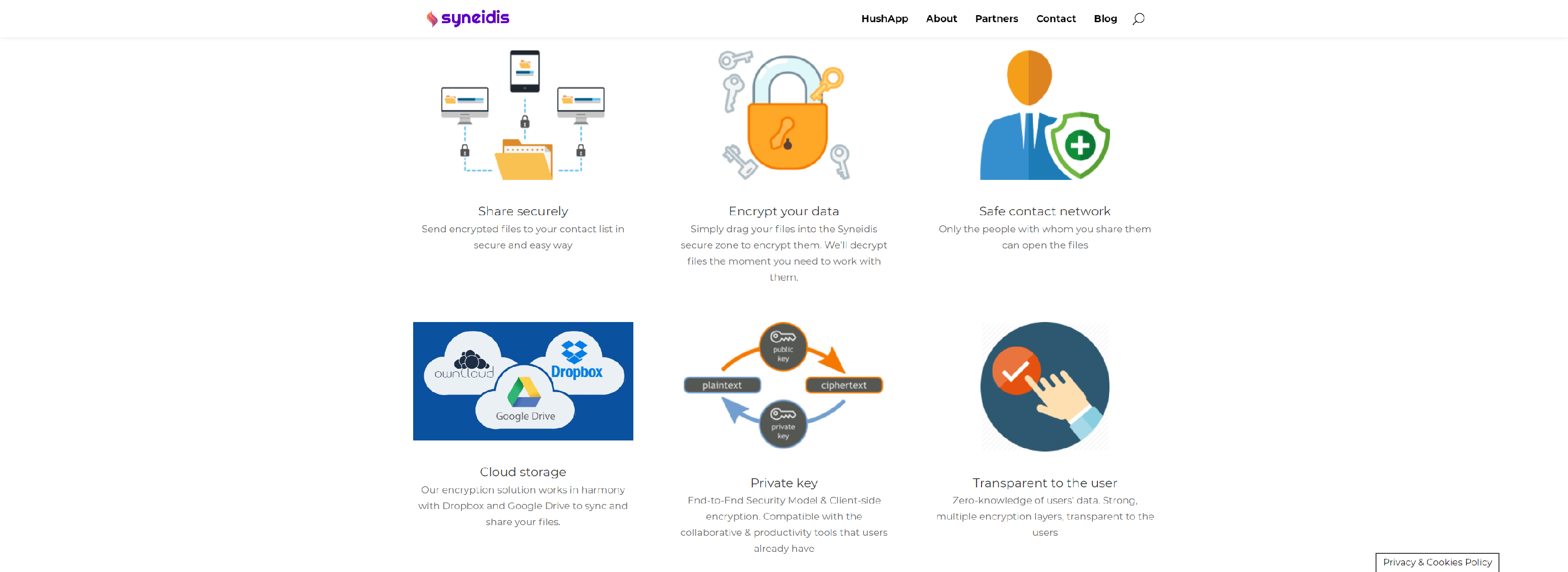
Syneidis, a European cybersecurity company we build powerful apps to help you protect your digital universe. Learn more core features share securely.
- Share securely
- Encrypt your data
- Safe contact network
- Cloud storage
- Private key
- Transparent to the user
CONTEXTIS
Context helps your business to manage cyber risk, and to deter, detect and respond to the most sophisticated cyber-attacks.
- Cyber Strategy & Transformation Programmes
- Risk Assessment & Compliance
- Security Architecture & Design
- Threat Assessment & Management
- Threat Hunting & Compromise Assessments
- Incident Management & Response
- Security Operations Consultancy
- Penetration Testing
- Simulated Targeted Attacks (Red Team, Blue Team)
- Active Directory Attack Resistance
- Mobile Application and Device Security
- Build and Configuration Reviews
- Source Code Reviews & Development Assurance
- Product Security Evaluation
- Compliance & Accreditation Schemes
- TestTracker
- Vulnerability Scanning
- Phishing
- Research Consultancy
- Cyber Security Training Courses
- User Awareness Training
- Simulations & Exercises
GROUP-IB
Leading provider of cybersecurity solutions – Threat Intelligence, antifraud, anti-APT.
- Security Assessment
- Red Teaming
- Pre-IR Assessment
- Compromise Assessment
- GIB Cyber School
- GIB Crypto
SECARMA

Secrama offer testing, consultancy, and training services to ensure your digital infrastructure is secure from cybersecurity threats.
Penetration Testing:
- Web Applications
- Infrastructure
- Mobile Applications
- Industrial Control Systems
- Embedded Devices (IoT)
- Wireless
- Databases
- Ransomware Protection
Security Assessment:
- Configuration Review
- Cyber Essentials
- Information Disclosure (OSINT)
- Social Engineering
- Vulnerability Scanning
Red Teaming:
- Red Team Assessment
Training:
- Secure Coding Workshop
Security Consultancy:
- Security Architecture Review
- Cybersecurity Half-Day Workshop
BASELINEIT
Baseline IT a leading cyber security company, which will ensure the high quality defence of the access to your company’s critical information.
- Security Assessment
- Security Operations Center
- Security Partner
- GDPR Compliance
CYTELLIGENCE
Cytelligence is a trusted cyber security advisor to hundreds of clients including top tier law firms, prominent multi-national corporations, government agencies, and private companies.
- Globally Accessible
- Extensive Experience
- Offensive Security
- Technology and Intelligence
- Effective Team
- Client Focus
IBM
IBM Security develops intelligent enterprise security solutions and services to help your business prepare today for the cyber security threats of tomorrow.
- Infrastructure and endpoint security services
- Security testing
- Incident response
- Identity and access management
- Data and application security
- Security intelligence and operations consulting services
- Security strategy, risk and compliance services
- Product Professional Services
KASPERSKY
Kaspersky Lab is committed to working with premier software and hardware vendors to provide the best security solutions possible.
- Threat Data Feeds
- APT Intelligence Reporting
- Tailored Threat Intelligence Reporting
- Financial Threat Intelligence Reporting
- Threat Lookup
- Cloud Sandbox
DELTAGON

Deltagon ensures the information security of e-communication and e-services, and secures business-critical information.
- Email encryption
- Secure electronic forms
- Secure information sharing
- Secure electronic signature
ARGUS-SEC
Argus Automotive Cyber Security develops solutions for vehicles that enable advanced connectivity features while protecting vehicles from being Hacked.
- Hreat analysis
- Risk assessment
- Vulnerability analysis
- Code review
- Penetration testing
- Incident response
- Cyber threat intelligence